3 minutes
The Essential Nmap Cheat Sheet for Quick Reference
The Essential Nmap Cheat Sheet for Quick Reference
Introduction
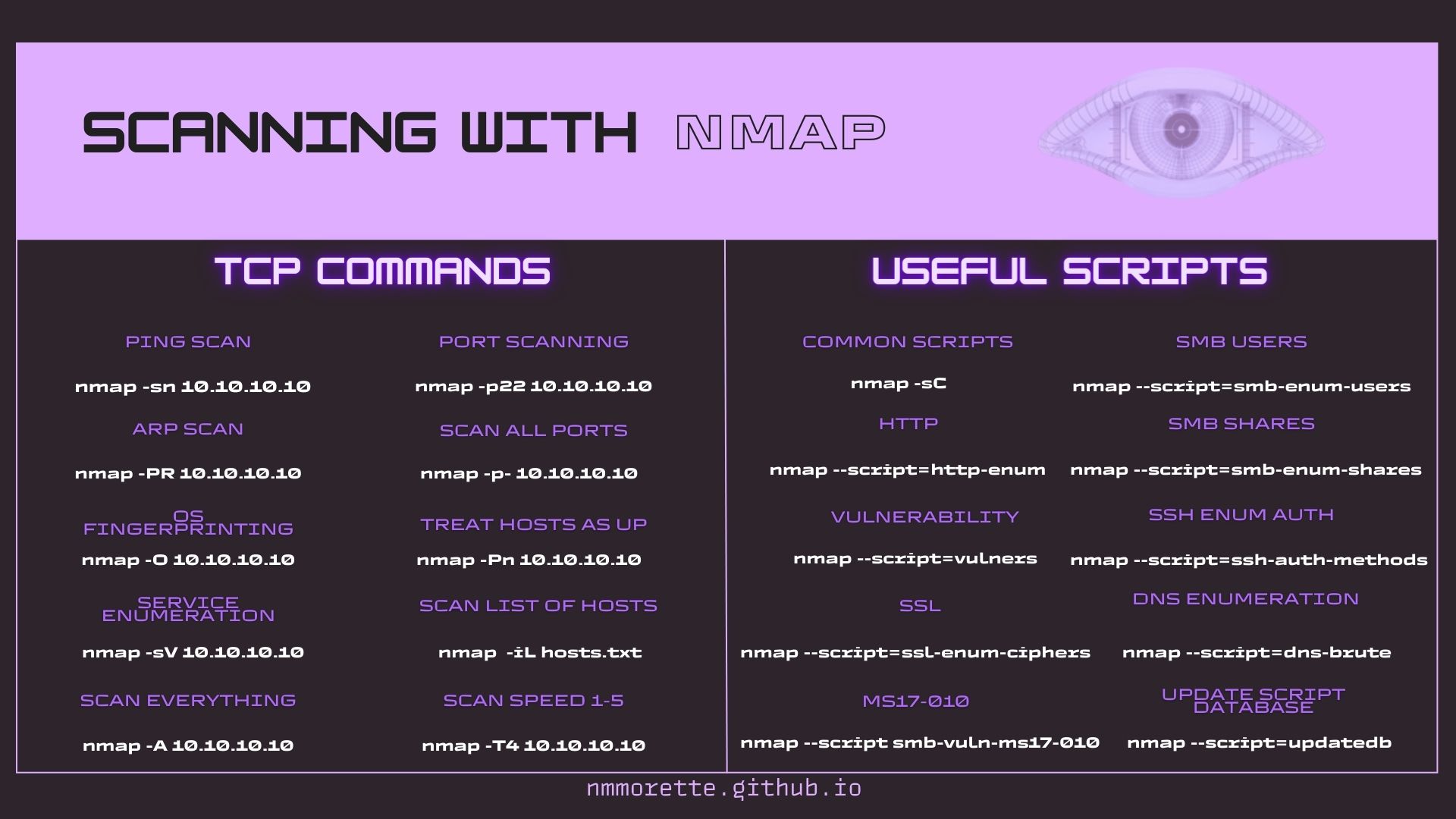
Nmap (Network Mapper) is an open-source tool for network exploration and security auditing. Widely used by network administrators, it’s crucial for vulnerability scanning and network inventory. This cheat sheet provides a quick reference to the most commonly used Nmap commands and options, ideal for both beginners and experienced users.
Basic Scanning Techniques
- Basic Network Scan:
Command:
nmap [target]- Use to quickly scan a target IP or domain.
- Scan Multiple IPs or Subnets:
Command:
nmap [target1, target2, etc.]- Handy for scanning multiple targets.
- Ping Scan (No Port Scan):
Command:
nmap -sn [target]- Useful for checking if the host is online without performing a port scan.
Advanced Scanning Options
- TCP SYN Scan (Stealth Scan):
Command:
nmap -sS [target]- Less intrusive and stealthier than a connect scan. - UDP Scan:
Command:
nmap -sU [target]- For scanning UDP ports. It’s slower but essential for a complete security audit. - Aggressive Scan:
Command:
nmap -A [target]- Provides a more comprehensive output including OS detection, version detection, script scanning, and traceroute. - Version Detection:
Command:
nmap -sV [target]- Detects the service version on the open ports.
Output Options
- Saving Output in a Specific Format:
Command:
nmap -oX [output.xml] [target](for XML format) - Other formats includeoNfor normal,oGfor grepable, andoAfor all. - Verbose Output:
Command:
nmap -v [target]- Provides more detailed output.
Scripts
Nmap’s scripting engine (NSE) is one of its most powerful and flexible features. It allows users to write (or use existing) scripts to automate a wide variety of networking tasks. This cheat sheet covers some of the most useful Nmap scripts for network discovery, vulnerability detection, and more.
Understanding Nmap Script Types:
- Default Scripts:
- Automatically used by Nmap for common tasks.
- Example:
nmap -sC [target](Runs default scripts) - Safe Scripts:
- Designed not to disrupt the target network.
- Example:
nmap --script safe [target] - Intrusive Scripts:
- Potentially disruptive, should be used with caution.
- Example:
nmap --script intrusive [target]
Popular Script Categories
- Discovery:
- Scripts for network and service discovery.
- Example:
nmap --script discovery [target]
- Vulnerability:
- Identifies known vulnerabilities.
- Example:
nmap --script vuln [target]
- Authentication:
- Tests for authentication mechanisms and weaknesses.
- Example:
nmap --script auth [target]
- Database:
- Specific scripts for database servers.
- Example:
nmap --script "database* and safe" [target]
- Malware:
- Checks for signs of infection or backdoors.
- Example:
nmap --script malware [target]
Using Script Arguments
- Some scripts accept arguments for more specific control.
- Example:
nmap --script [script-name] --script-args=[arg]=[value] [target]
Combining Scripts and Scan Techniques
- Scripts can be combined with standard Nmap scan techniques.
- Example:
nmap -sV --script=default,vuln [target]
Output and Debugging
- Use verbose and debugging options for detailed script output.
- Example:
nmap --script [script] -d [target](debugging mode) - Example:
nmap --script [script] -v [target](verbose mode)