3 minutes
Hackerviser Secure Command - Warmup Stage I
Secure Command
Introduction
Secure Shell (SSH) is a protocol used to securely access and manage devices on a network. It encrypts data to protect confidentiality and integrity, making SSH a preferred option over Telnet for remote administration.
What is SSH?
SSH is a cryptographic network protocol that facilitates secure communication over an unsecured network. Originally designed as a replacement for insecure protocols like Telnet, SSH ensures confidentiality and integrity of data exchanged between two networked devices. It provides a secure channel over an unsecured network by encrypting the data during transmission.
Key Features and Benefits:
- Encryption: SSH employs strong encryption algorithms to secure communication, thwarting eavesdropping and data tampering attempts.
- Authentication: It supports various authentication methods, including passwords, public-key cryptography, and multi-factor authentication, ensuring robust access control.
- Port Forwarding: SSH’s port forwarding capability allows users to securely tunnel traffic between local and remote systems, facilitating secure access to internal services.
- File Transfer: With tools like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol), SSH enables secure file transfer between systems.
- Remote Administration: System administrators utilize SSH to manage servers and network devices remotely, executing commands and performing administrative tasks securely.
- Tunneling: SSH tunneling enables users to bypass network restrictions and securely access services hosted on remote networks.
- Automation: SSH can be seamlessly integrated into automated scripts and workflows, streamlining repetitive tasks and enhancing productivity.
The Future of SSH:
Despite being over two decades old, SSH continues to evolve, adapting to the changing needs of modern computing environments. With the emergence of cloud computing and distributed systems, SSH remains indispensable for secure remote access and management.
Looking ahead, advancements in cryptography and networking technologies will likely further enhance SSH’s security and performance, ensuring its relevance in the ever-evolving landscape of IT infrastructure.
Conclusion:
SSH’s enduring popularity is a testament to its reliability, security, and versatility. Whether you’re a system administrator managing a fleet of servers or an individual user accessing your personal computer remotely, SSH empowers you with a secure and seamless remote access solution.
As we navigate the complexities of the digital age, SSH stands firm as a beacon of trust, enabling us to traverse the vast expanse of the internet securely and with confidence.
Tasks
Which port(s) are open?
Usually sshruns in port 22, but let’s run nmap without a specific port.
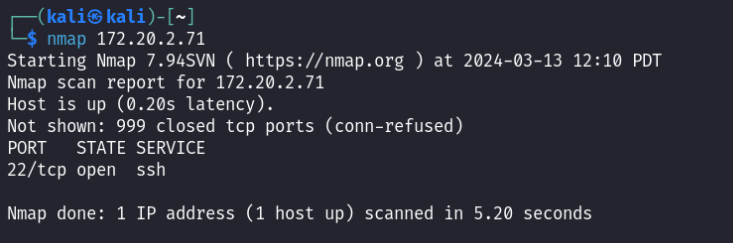
Port 22 is open.
What is the running service name?
We got the service name with nmap
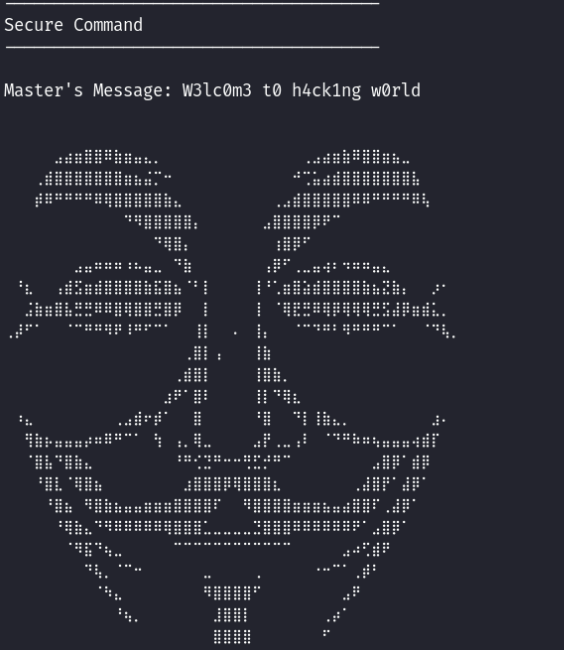
What is “Master’s Message” when connecting to SSH with hackviser:hackviser credentials?
Connection with ssh:
What is the command to change user in Linux?
The command to change the current user in Linux is su, which stands for “switch user” or “substitute user”. By default, when you run su without any arguments, it switches to the root user. If you want to switch to another user, you can specify the username as an argument.
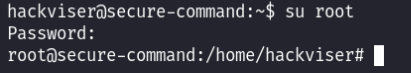
What’s the password for root user?
Just tried to change to root with password root:
What is the parameter of the ls command that shows hidden files?
The parameter of the ls command that shows hidden files is -a or --all. When you use ls -a or ls --all, it lists all files, including hidden files and directories. Hidden files and directories in Unix-like operating systems are those whose names start with a dot (.).
What is the master’s advice?
Looking for files, I found the hidden file .advice_of_the_masterin the root folder.