3 minutes
Hackerviser 007 - Warmup Stage I
007
Introduction
Remote Desktop Protocol (RDP) has become an indispensable tool in today’s digital landscape, enabling seamless remote access to computers and servers from anywhere in the world.
What is Remote Desktop Protocol (RDP)?
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft, designed to facilitate remote desktop connections between computers over a network connection. It allows users to access and control a remote computer as if they were physically present at the machine. RDP operates on TCP/IP and is available on most versions of Windows operating systems.
Benefits of RDP
- Remote Access: RDP enables users to remotely access their desktops, laptops, or servers from anywhere with an internet connection, providing flexibility and convenience for remote work scenarios.
- Collaboration: RDP allows multiple users to connect to a single computer simultaneously, fostering collaboration and teamwork, especially in remote or distributed teams.
- Resource Sharing: RDP enables the sharing of resources and applications across multiple devices, optimizing resource utilization and enhancing productivity.
- Security: RDP incorporates robust encryption and authentication mechanisms to ensure secure remote connections, protecting sensitive data from unauthorized access.
Best Practices for Using RDP
- Enable Network-Level Authentication (NLA): NLA enhances security by requiring users to authenticate before establishing a remote desktop session, mitigating the risk of unauthorized access.
- Use Strong Passwords: Ensure that strong, unique passwords are set for RDP connections to prevent brute-force attacks and unauthorized access to remote systems.
- Implement Firewall Rules: Configure firewall rules to restrict RDP access to trusted IP addresses or networks, reducing the risk of unauthorized access from external sources.
- Keep Software Updated: Regularly update RDP client and server software to patch security vulnerabilities and ensure the latest features and enhancements are available.
Conclusion
Remote Desktop Protocol (RDP) revolutionizes the way we access and manage remote systems, offering unparalleled convenience, flexibility, and security. Whether you’re a remote worker, IT administrator, or business owner, leveraging RDP can streamline operations, enhance collaboration, and drive productivity. By following best practices and deploying RDP securely, you can unlock the full potential of remote access technology and empower your workforce to thrive in today’s interconnected world.
Warmup - 007 - Tasks
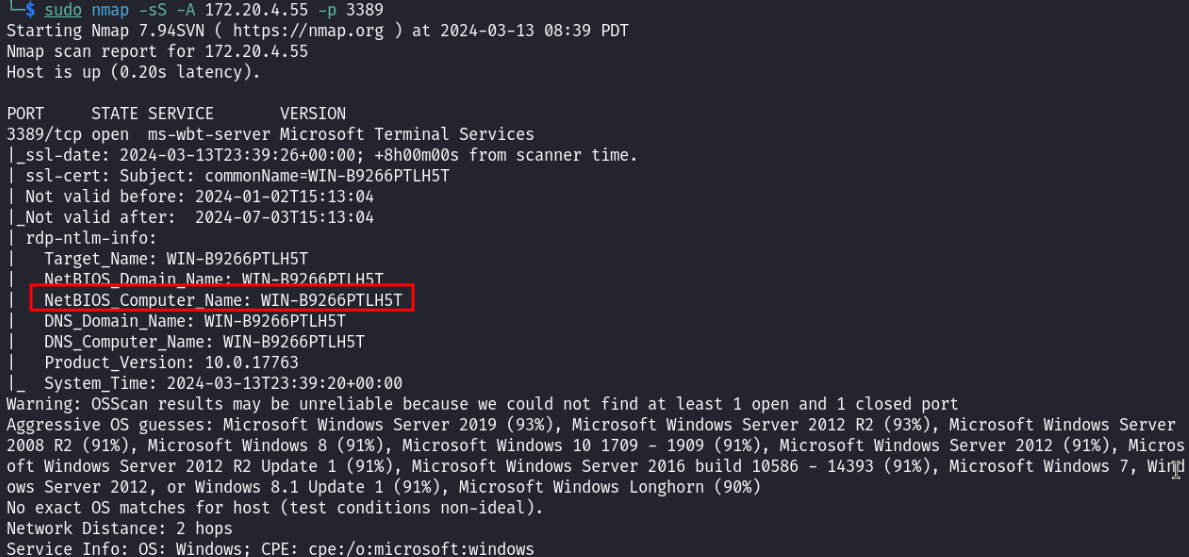
What is target hostname?
Usually RDP is on port 3389, you could run nmapdirectly to this port, but Let nmap with -Ato get info about the service.
What does RDP stands for?
Remote Desktop Protocol
What is usually the most privileged username in Windows?
In Windows systems, the most privileged username is typically “Administrator.” This account has full access to system resources, including the ability to install software, modify system settings, and perform administrative tasks. It is important to safeguard the Administrator account with a strong password and limit its usage to necessary administrative tasks to ensure the security of the system. Additionally, it’s recommended to create a separate, less privileged user account for everyday tasks to minimize the risk of accidental or malicious actions.
Whats the Windows version?
Let’s attempt to establish an RDP connection to the target machine using the guessed Administrator user credentials.
Various tools exist for setting up an RDP connection to a remote computer. Microsoft Remote Desktop, FreeRDP, rdesktop, and Remmina are among the options available for RDP connections.
For the task at hand, let’s utilize xfreerdp , usually pre-installed in Kali Linux. Since we dont have a password, lets try to connect with administrator and no password.
xfreerdp /u:administrator /v:172.20.4.55
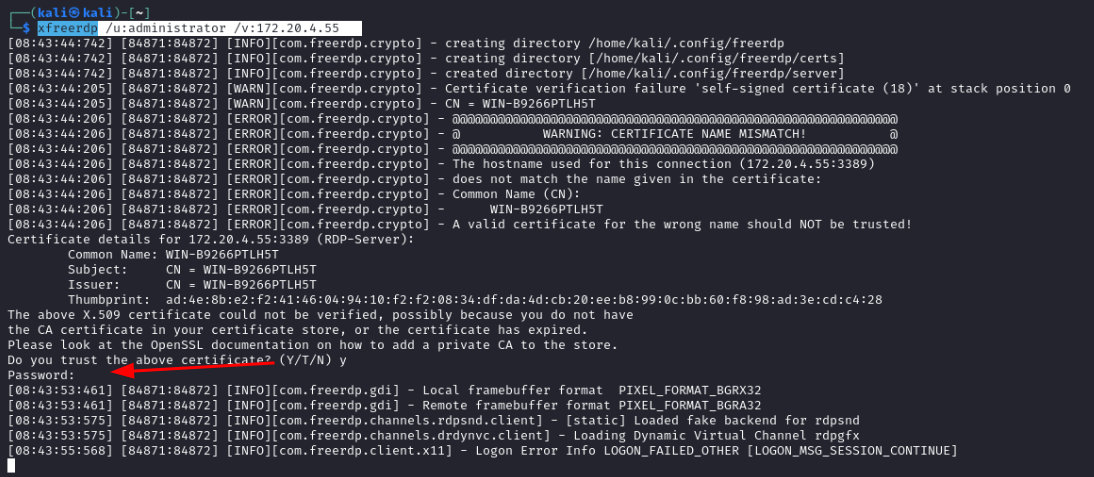
With the RDP connection open, lets use the command winverto check the windows version.
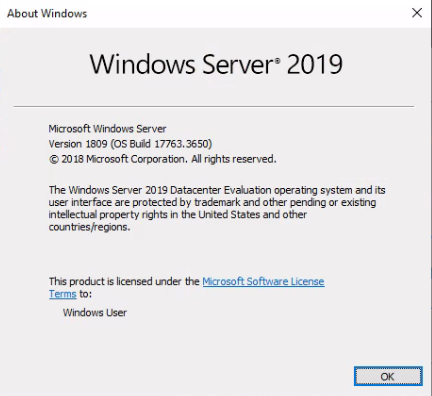
It is also possible to get this info in Powershell
Get-ComputerInfo | Select-Object WindowsVersion
What is the name of the suspect folder under the C:\ directory?
Checking the C:\ directory, there is a non common/default windows folder:
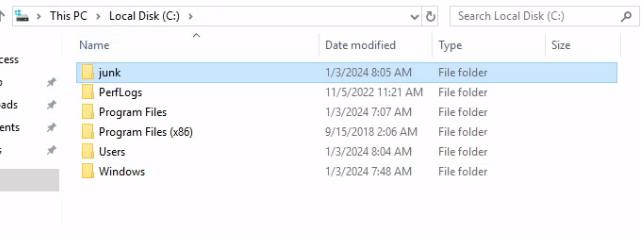
Which user owns the junk folder?
It is possible to check a owners folder in Properties>Security>Advanced: