3 minutes
Hackerviser Arrow - Warmup Stage I
Arrow
Introduction
Telnet, short for Telecommunication Network, is a protocol used for remote terminal connections, allowing users to interact with a computer or network device over a network. Despite its age and simplicity, Telnet still plays a role in various networking scenarios. However, its lack of security features makes it a risky choice in today’s cybersecurity landscape.
What is Telnet?
Telnet operates on the Application Layer of the OSI model and uses a client-server architecture. It allows a user to establish a terminal session on a remote host, enabling them to execute commands as if they were directly connected to the system’s console.
How Does Telnet Work?
Telnet works by establishing a TCP connection between a client and a server. Once the connection is established, the client sends commands and keystrokes to the server, which executes them and returns the results to the client. Telnet sessions typically operate on port 23, though this can be configured.
Security Risks Associated with Telnet:
- Lack of Encryption: Telnet transmits data, including usernames, passwords, and commands, in plain text. This makes it susceptible to eavesdropping and interception by malicious actors.
- Authentication Vulnerabilities: Telnet authentication mechanisms are often weak or nonexistent, leading to the risk of unauthorized access. Default credentials are commonly used, further exacerbating this issue.
- Session Hijacking: Since Telnet sessions lack encryption, attackers can potentially hijack active sessions, allowing them to manipulate or observe the ongoing communication between the client and server.
- Man-in-the-Middle Attacks: Telnet sessions are vulnerable to man-in-the-middle (MITM) attacks, where an attacker intercepts and modifies the communication between the client and server, leading to data manipulation or theft.
Alternatives to Telnet:
- SSH (Secure Shell): SSH provides encrypted communication sessions over a network and offers strong authentication mechanisms, making it a more secure alternative to Telnet.
- Remote Desktop Protocol (RDP): RDP allows users to remotely access and control Windows-based systems, offering features like encryption and multi-factor authentication.
- Web-based Interfaces: Many network devices and servers provide web-based interfaces for remote management, offering secure communication over HTTPS.
Conclusion
While Telnet once served as a fundamental tool for remote terminal access, its inherent security vulnerabilities make it unsuitable for modern network environments. Organizations should transition to more secure alternatives like SSH and implement best practices to mitigate the risks associated with remote access protocols. By understanding the functionality and security risks of Telnet, network administrators can make informed decisions to safeguard their systems and data.
Warmup - Arrow - Tasks
Which port(s) are open?
Let’s start running nmap to find the open ports:
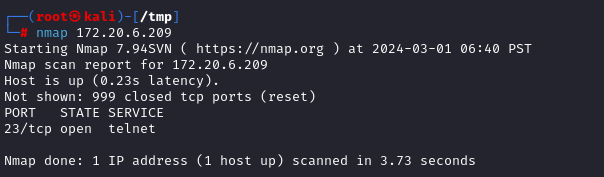
What is the running service name?
Now let’s improve or scan to get more info:
nmap -sS -A 172.20.6.209 -p 23
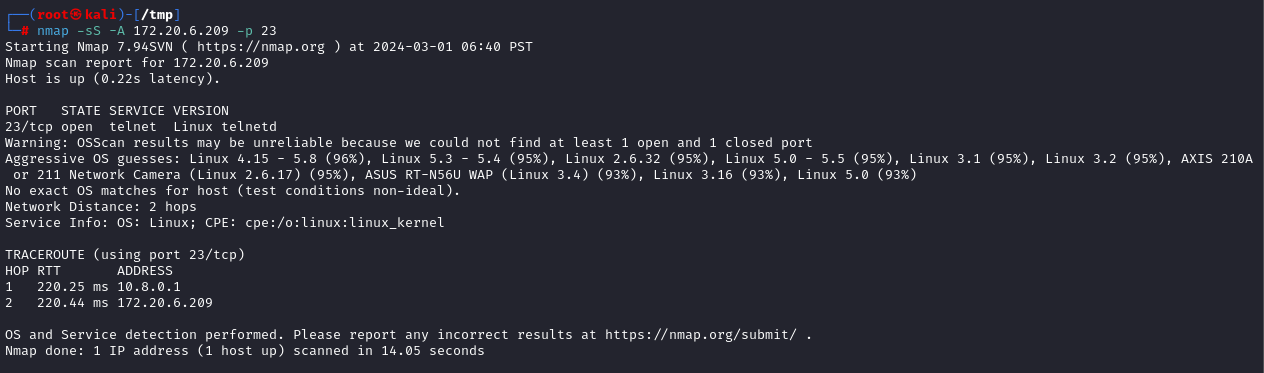
Now we found the service running on port 23 is telnet.
What’s the username:password you use to connect to telnet?
First, attempt to establish a direct connection using Telnet:
telnet 172.20.6.209
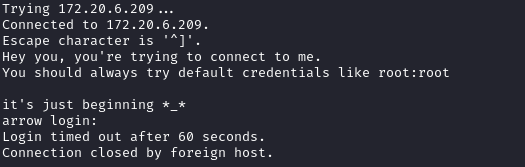
After attempting to establish a Telnet connection, it’s possible to observe a hint suggesting the use of default credentials.
What is the working directory location when you connect to telnet?
In Linux system to find the folder you are in just type pwd